Na zahtevo prijateljev in uporabnikov vam bom predstavil tukaj kako si doma namestit WEBScada – Pametna Hiša vizualizacija za spet za CybroTech Kontrolerje – Robotina.si oz. Robitina.com – CybroTech.com – PCS-NET nadzor IP kamere, Centralno gretje, Klima, Luči, TV sprejemnik – Statelit Astra 1,2,3 in video snemalnik. – popravek za Raspbian 11 Linux / 2022 NI VEČ RAČUNA PI DIREKTNO GENERIRAJTE VAŠ ADMIN RAČUN KARKOLI NPR. webscada (PS Raspbian 11 nima po defaultu nameščen python2 in pip oz. pip2 – namestite python2 in določite python-is-python2, šele pol namestite vse potrebne module in webscada!)
Osebno nisem računalničar in to je moja logika postavitve strežnika rasbian in namestitev web scade! Vsekakor bo kakšen strokovnjak na področju ITS oz. informacijskih sistemov menil, da bostaja boljši način. Zato je najbolje da se obrnete na pomoč na staneh Robotina.si:
Za vse Uredniške račune, Avtorske račune lahko dostopate do mojih člankov in objav preko URL: https://perc.ddns.net – privatni in javni blog wordpress, bbForum in ostale fukncionalnosti strežnikov z nadzornimi ploščami (uporabite za dostop unikodo in vaše uporabniško ime)!
POZOR POMEMBNO OPOZORILO SPODNJI PODTOPEK NAMESTITEVE WEB SCADA CYBROTEC KONTROLERJI VELJA ZA RAZLIČNICO OPERACIJSKEGA SISTEMA UBUNTU 18, RASPBIAN 10 IN DEBIAN 10
V KOLIKOR BOSTE NAMESTILI OPERACIJSKI SISTEM UBUNTU 20, RASPBIAN11 DEBIAN11 PO DEFAULTU PYTHON2 NI NAMEŠČEN IN V REPOSITORIJIH JE VEČINA MODULOV MENJANIH OZ. NE OBSTAJAJO VEČ ZA PYTHON2 JIH JE POTREBNO NAMESTIT IZ SURCE DATOTEKE!!!! APACHE WSCGI, MODULI PYTHON MYSQL itd…
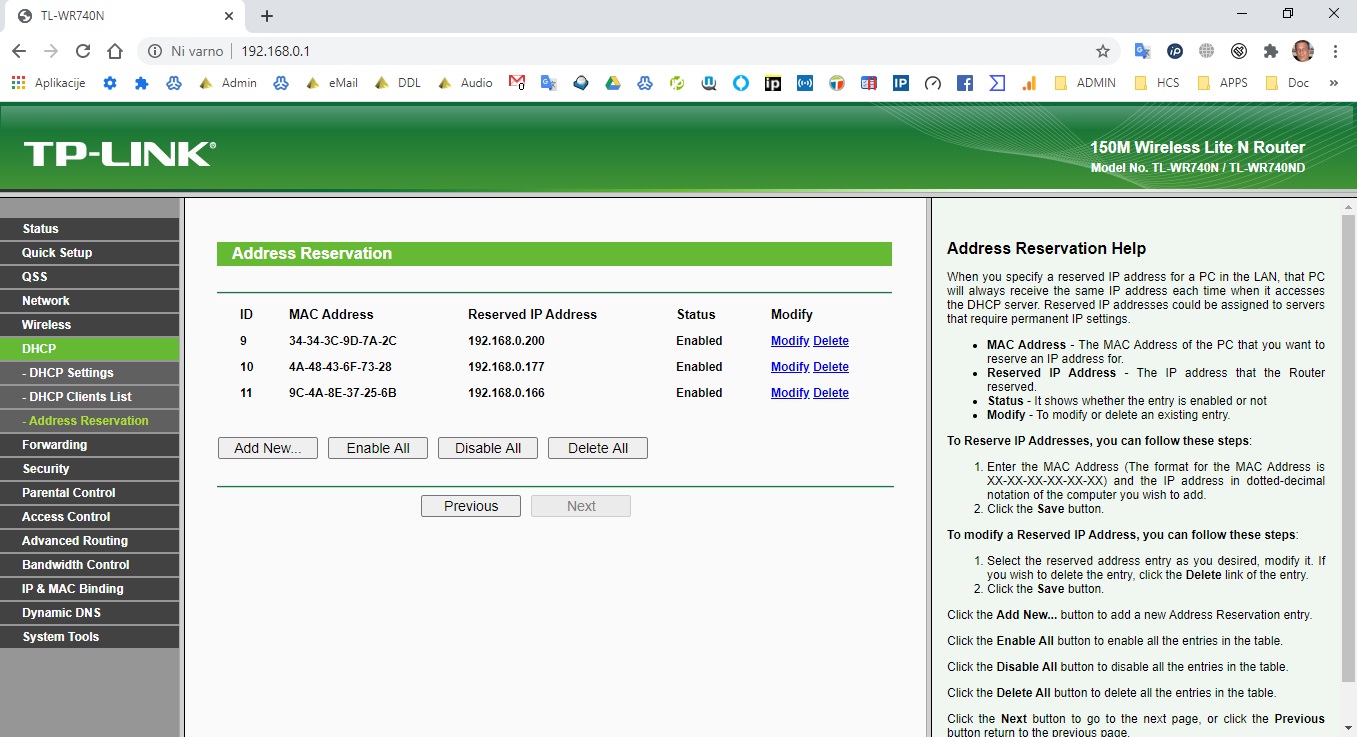
Rezervirajte na vašem usmerjevalniku oz. routerju za vašo napravo PI-3-4 Raspberry – Če imate TPLink router in dinamični internet (javno) v meniju Dynamic DNS nastavite še noip.com. Za ostale lahko namestite v vaš raspberry PI mini server aplikacijo za linux.
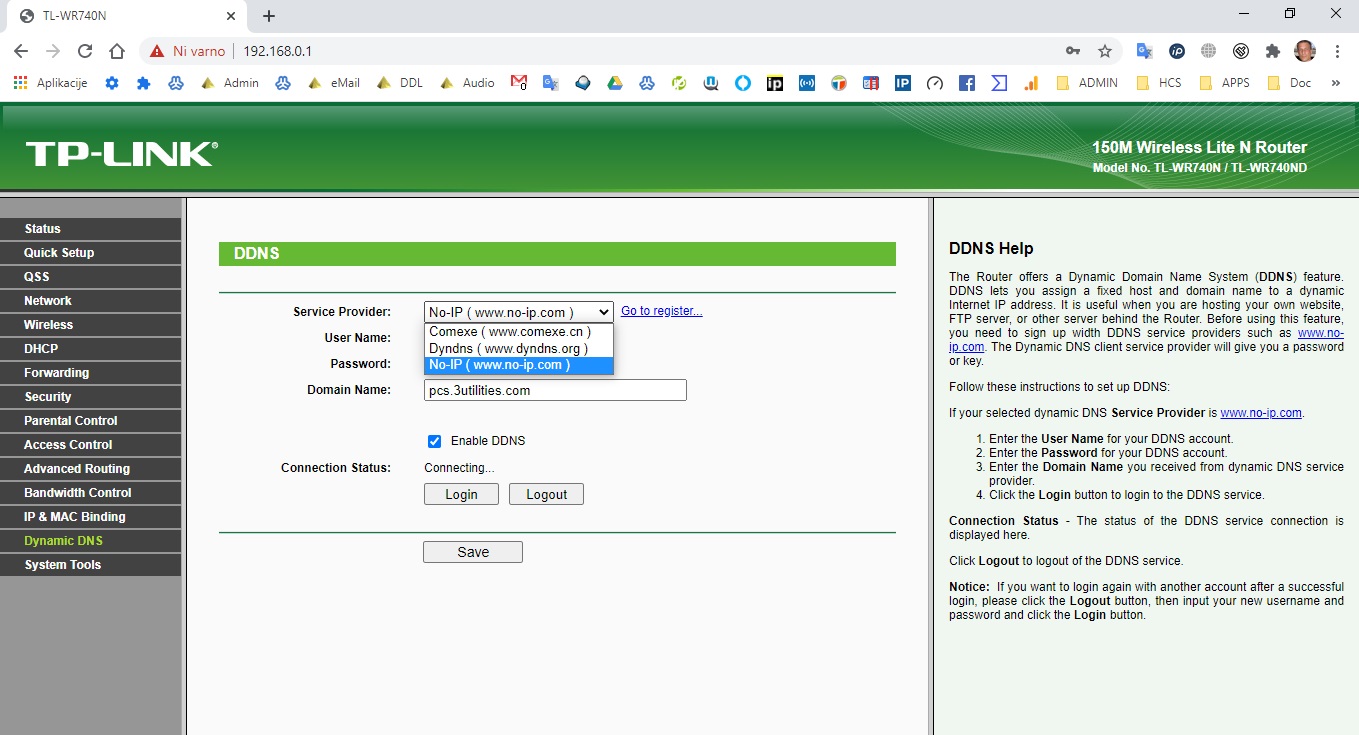
Ko namestite celoten rasbian linux minimal install obvezno postopek kako namestit na PI4 noip.com DUC aplikacijo – da boste dobili namesto IP domeno za vaš mini serverček – registriraje na doemeni noip.com vaš račun brezplačno.
webscada@mojascada :~ $
cd /usr/local/src/
sudo wget http://www.no-ip.com/client/linux/noip-duc-linux.tar.gz
tar xf noip-duc-linux.tar.gz
sudo rm noip-duc-linux.tar.gz
cd noip-2.1.9-1/
sudo make install
Your username is: noip.com uporabniško ime
Your password is: noip.com pristopno geslo
cd /etc/
sudo nano rc.local
# kopijaj to zraven direktive oz. dodaj spodaj sudo nano noip2
# rc.local
sudo -u webscada /home/linuxter/app/scgi_server/src/run_scgi_server.py
# TAM ODKOMENTIRAJTE KOT STE NAMESTILI NA PI4 WEB SCADO PRIMER
sudo noip2
# SHRANI IN PONOVNI ZAGON PI
sudo shutdown -r now
sudo noip2 -S💡 ZAČETEK PRIPRAVA SERVERJA
Pomembno, za Raspbian 10 Buster minimal install obvezno prvo namestite Apache, MariaDB server in client, php7.4 in vse potrebne python module in dodatno programsko opremo!
01) Potrebna strojna oprema za spletni strežnik Raspberry Pi
potrebovali boste:
- Raspberry Pi seveda. Potrebovali boste tudi napajalno enoto in etui.
- Tipkovnica USB, miška USB, monitor s povezavo HDMI in kabel HDMI.
- Čitalnik kartic SD.
- USB ključek za shranjevanje podatkov, čeprav to ni obvezno, saj lahko za shranjevanje podatkov uporabite kartico SD. Zdaj na novih PI4 namesto SD kartice lahko kupite tudi USB3 plavi priključek od raspberry SSD Disk nrp. 2-TeraBajta – 2048 MB (namesto sd kartice zapečete OS Rasbian na USB Disk)
- Ethernetni kabel za povezavo RPi z usmerjevalnikom / brezžično dostopno točko ali Ethernet stikalom.
02) Operacijski sistem
Namestite operacijski sistem – PRENOS RASBIAN LINUX 32BIT TUKAJ
Ta stran opisuje prenos in namestitev operacijskega sistema, potrebnega za vaš Raspberry Pi. https://www.raspberrypi.org/
Za Raspberry Pi boste potrebovali kartico MicroSD z operacijskim sistemom. Kartico MicroSD lahko kupite na različnih komercialnih spletnih mestih z že nameščenim operacijskim sistemom, vendar je ni težko naložiti in namestiti sami, če ima vaš domači računalnik bralnik SD.
Če želite sami namestiti operacijski sistem, prenesite najnovejšo datoteko Raspbian iz: https://www.raspberrypi.org/downloads/raspberry-pi-os/
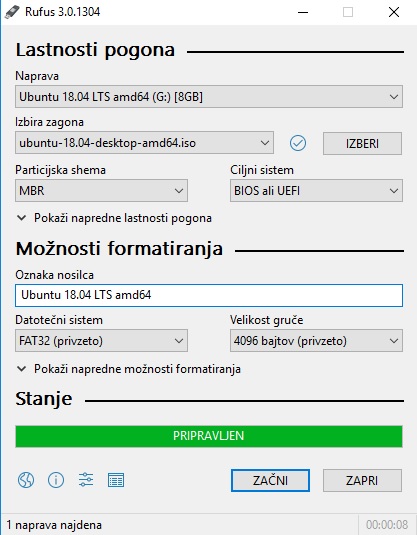
Lahko prenesete NOOBS in ga namestite na kartico SD. NOOBS je namestitveni program operacijskega sistema, ki nekoliko olajša postopek namestitve. Lahko pa prenesete sliko Raspbian in jo namestite na kartico SD kar je po mojem najbolje minimal install = image Rasbian lite!!!!!
Oblikovanje kartice SD
Če je bila kartica SD uporabljena že prej, jo boste morali formatirati, preden boste kar koli drugega storili. Če želite formatirati kartico SD v računalniku z operacijskim sistemom Windows, lahko uporabite format pomnilniške kartice SD, ki ga lahko prenesete od tukaj:
https://www.sdcard.org/downloads/formatter/ ali po moje je najbolje Rufus!!!!
Opomba: Pri uporabi tega pripomočka bodite previdni, saj lahko v računalniku formatirate napačen pogon.
Nameščanje NOOBS
Razširite datoteko za prenos, da dobite datoteke za kartico SD, nato pa jih s pomočjo raziskovalca datotek kopirajte na kartico SD. Izvlečene datoteke so lahko znotraj mape, v tem primeru kopirajte obrazec datotek znotraj mape in ne same mape.
Izvlecite kartico SD in jo vstavite v Raspberry Pi.
Ko vstavite kartico SD, pritrdite napajalnik, tipkovnico, miško in monitor – Raspberry Pi se bo zagnal. Izberite operacijski sistem Raspbian. Popeljal vas bo skozi vrsto nastavitvenih faz, ki bodo posodobile programsko opremo na najnovejšo različico, in vam zastavile različna vprašanja o zahtevani konfiguraciji za jezikovne nastavitve, vrsto tipkovnice itd.
Namestitev Raspbian iz prenosa
Raspbian lahko namestite neposredno na vaš Raspberry Pi, namesto da namestite prek NOOBS.
Za kartico SD potrebujete programsko opremo za slikanje.
Win32DiskImager je običajna izbira za osebni računalnik z operacijskim sistemom Windows in ga lahko prenesete iz:
http://sourceforge.net/projects/win32diskimager/
ali bolje
https://rufus.ie/
Prenesite npr. Win32DiskImager in razpakirajte datoteko ali bolje je Rufus po moje. Datoteko exe lahko zaženete celo iz pogona USB ali naložite Rufus in jo odprete.
Prenesite Raspbian in za dostop do slike razpakirajte preneseno datoteko.
Morda boste morali najprej formatirati kartico SD. Ko je formatiran, lahko z Win32DiskImager zapišete sliko Raspbian na kartico SD.
Izberite slikovno datoteko, ki ste jo izvlekli, in v polju naprave izberite črko pogona kartice SD.
Prepričajte se, da ste izbrali pravilno črko pogona.
Kliknite Write in počakajte, da se slika zapiše na kartico SD.
Zaprite programsko opremo za preslikovanje, odstranite kartico SD in jo vstavite v Raspberry Pi.
ZAPEČITE NAJNOVEJŠI OS RASPBIAN = https://www.raspberrypi.com/software/operating-systems/
obvezno minimal install os !!!
03) V računalniku Win ali MACu nastavite povezavo z oddaljenim namizjem (po izbiri – boljša varianta WebMin)
Ta stran oz. poglavje opisuje, kako namestite in nastavite oddaljeno namizje na Raspberry Pi, tako da lahko dostopate do svojega Pi, ne da bi ga povezali z monitorjem, tipkovnico ali miško.
Zaženite svoj Pi
Priključite tipkovnico USB, miško USB in s kablom HDMI povežite monitor z Raspberry Pi.
Napajalnik priključite na Raspberry Pi in se prepričajte, da je kartica MicroSD na mestu.
Priključite svoj Ethernet kabel na Raspberry Pi.
Vklopite Raspberry Pi.
Nato se Raspberry Pi zažene.
Privzeto uporabniško ime in geslo je uporabniško ime pi z geslom raspberry.
Nastavite povezavo z oddaljenim namizjem
Povezava z oddaljenim namizjem vam omogoča nadzor vašega Pi-ja iz osebnega računalnika, kot da bi bil fizično povezan z računalnikom. To pomeni, da lahko odpravite povezave monitorja HDMI, miške in tipkovnice.
Xrdp se mi zdi dober način za to, čeprav se nekateri uporabniki raje odločijo za brezglavo in popolnoma odstranijo grafični uporabniški vmesnik po mojem najbvoljši način. Nato se povežite v Pi s pomočjo SSH. Neuporaba grafičnega uporabniškega vmesnika ima lahko prednosti, ker bi lahko imeli potem dostop do več pomnilnika. Vendar se mi zdi uporaba GUI veliko bolj priročna. Jaz bi se odločil po moje, če bi nameščal Scado na PI vsekakor minimal install, in ob prvem zagonu povezava SSH ter v nastavitvah raspi-config bi za GPU v advance nastavitvah dal 16 Rama!!! Ne pozavite ob prvem zagonu localization odkljukajte poleg GB utf8 še SL_SI_UTF8 in uni spodnji SL_SI…….
Če se želite povezati z Raspberry Pi iz oddaljenega računalnika, lahko na Pi namestimo xrdp in se nato iz računalnika samo povežemo z njegovim naslovom ip.
Najprej namestite xrdp z uporabo naslednjega, ko ste v terminalu:
sudo apt install xrdpPoiščite ip naslov vašega Raspberry Pi z naslednjim ukazom v terminalu:
ifconfigPoiščite eth0, ob predpostavki, da ste z lokalnim omrežjem povezani z eth0, in videli bi naslov IP, ki bo v obliki lahko pa tudi wlan oz. wifi po želji:
192.168.1.82Zdaj lahko v sistemu Windows/MacBook ali PC nastavite novo povezavo z oddaljenim namizjem.
Na namizju ustvarite novo datoteko z razširitvijo .rdp.
Ustvarjanje datoteke rdp v računalniku
Z desno miškino tipko kliknite novo ustvarjeno datoteko .rdp in izberite Uredi.
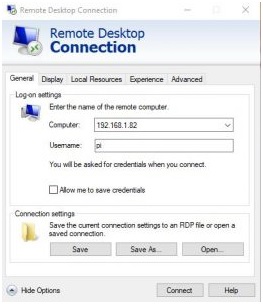
V polje za vnos računalnika vnesite ip naslov vašega Raspberry Pi in vnesite tudi uporabniško ime, ki je v tem primeru pi.
Če to shranite in nato dvokliknete datoteko .rdp, vam bo omogočila povezavo z vašim Raspberry Pi in prijavo z uporabniškim imenom pi in geslom raspberry.
Raspberry Pi bo zdaj šel skozi vrsto zaslonov za konfiguracijo, ki so precej naravnost naprej.
Ko končate z nastavitvijo in namestitvijo najnovejših posodobitev, lahko odpravite priključke tipkovnice, miške in HDMI na Raspberry Pi in do Pi boste lahko dostopali od koder koli v lokalnem omrežju.
04) Konfigurirajte Raspberry Pi
Obstaja nekaj stvari, ki jih moramo nastaviti kot del osnovne konfiguracije Raspberry Pi. Za to raje uporabljam vmesnik GUI, ki je na daljavo povezan z računalnikom Pi.
Na zaslonu menija bi morali videti Nastavitve -> Konfiguracija Raspberry Pi. Kliknite na to, da se prikaže zaslon konfiguracije.
Druga metoda je uporaba pripomočka za konfiguracijo Raspberry Pi iz terminala z vnosom:
sudo raspi-configTa ima nekoliko naprednejše funkcije, ki jih boste morda želeli spremeniti.
Spremenite geslo Pi npr. v pi to samo začasno dokler ne uštimamo vse!!! Jaz rajši osebno delam preko terminala program putty oz. jaz uporabljam SMARTFTP – TA PROGRAM BOSTE DOBIL V DDL ENIGMA (DOŽIVLJENSKA LICENCA!!!)
Spremenite geslo – Password za privzeto uporabniško ime pi v nekaj drugega, da izboljšate raven varnosti, če boste uporabljali račun pi, ma jaz vam to odsvetujem, samo za začetek za lažje delo spremenite geslo za uporabnika pi namesto raspberry geslo dajte v pi.
Spremenite ime gostitelja – hostname – raspberry v vaše karkoli npr. webscada!!!
Preklopite na nekaj bolj primernega, kot je npr. v tem primeru za webscado v “webscada” ali “mojascada” po vaši izbiri.
Preverite nastavitve vmesnikov – Interfaces settings
Pojdite na zavihek vmesnika “interface” in preverite, ali so vsi vmesniki onemogočeni se pravi enable SSH!!!
Običajno uporabljamo povezavo z oddaljenim namizjem, če pa uporabljate SSH, se prepričajte, da je SSH omogočen – po mojem je to najboljša varianta, po želji sami se odločite ali boste delali preko terminala SSH ali Oddaljenega Namizja xrdp.
Posodobite svoje lokalne nastavitve – Se pravi Jazik ne pozabit odkljukat sl_si_UTF8 in še tistega spodaj ali važno je ta je ta sl si utf 8 odkljukan!
Poskrbite, da bosta vaša lokacija in časovni pas pravilno nastavljeni.
Shranite konfiguracijo in znova zaženite
Prepričajte se, da so spremembe shranjene, in znova zaženite Raspberry Pi.
Raspberry Pi lahko znova zaženete s terminala z uporabo:
sudo shutdown -r nowali znova zaženite z uporabo:
sudo rebootali samo zaustavitev sistema z uporabo:
sudo shutdown -h nowKo ste priklopi na TV vaš pi in tipkovnico se prijavli v terminal nastavite spodaj:
HOSTNAME MENJAJ V SVOJE NPR. webscada ali karkoli po vaši izbiri in za lažje delo na začetku menjajte password oz. geslo v pi in potrdi pi za lažje delo. Pol lahko ko končate samo zaklenete račun pi.

SSH ENABLE ! VLOLOPI
GPU ram spremeni iz 64 v 16

SPREMENI V NAŠO LOKACIJO UTF8 SL SI



05) Raspberry Pi povežite z omrežjem in usmerjevalnikom
Zdaj, ko smo namestili Raspbian in končali osnovno konfiguracijo, lahko zdaj končamo s povezovanjem z vašim usmerjevalnikom.
Najprej povežite omrežje z Raspberry Pi in posodobite tako, da vnesete v terminalu (npr. putty ali SmartFTP):
sudo apt-get updateNato nadgradite tako:
sudo apt-get upgradeZdaj lahko omrežje nastavimo tako, da Raspberry Pi uporablja fiksni naslov IP, ki se ob ponovnem zagonu usmerjevalnika ne spremeni (To obvezno v usmerjevalniku razervirajte oz. v vašem routerju).
Najprej poiščite naslov MAC in naslov IP vašega Raspberry Pi z ukazom:
ifconfigNaslov MAC je enolična številka, dodeljena omrežnim vmesnikom – to je omrežni naslov, ki ga lahko uporabimo za povezavo z naslovom IP.
Naslov MAC bo videti nekako tako: b8:27:eb:ad:31:3c
Naslov IP bo videti nekako takole: 192.168.1.75
Ko dobite naslov MAC in IP, se morate prijaviti v usmerjevalnik. Nekje v menijskem sistemu bi morali najti naprave v svojem omrežju. To je seveda odvisno od vašega usmerjevalnika in morda boste morali poiskati dokumentacijo zanj. Vaš usmerjevalnik naj prikaže Raspberry Pi z imenom gostitelja, naslovom IP in MAC.
Če se na Raspberry Pi vedno sklicujete z imenom gostitelja, ne bo pomembno, ali se bo naslov IP spremenil.
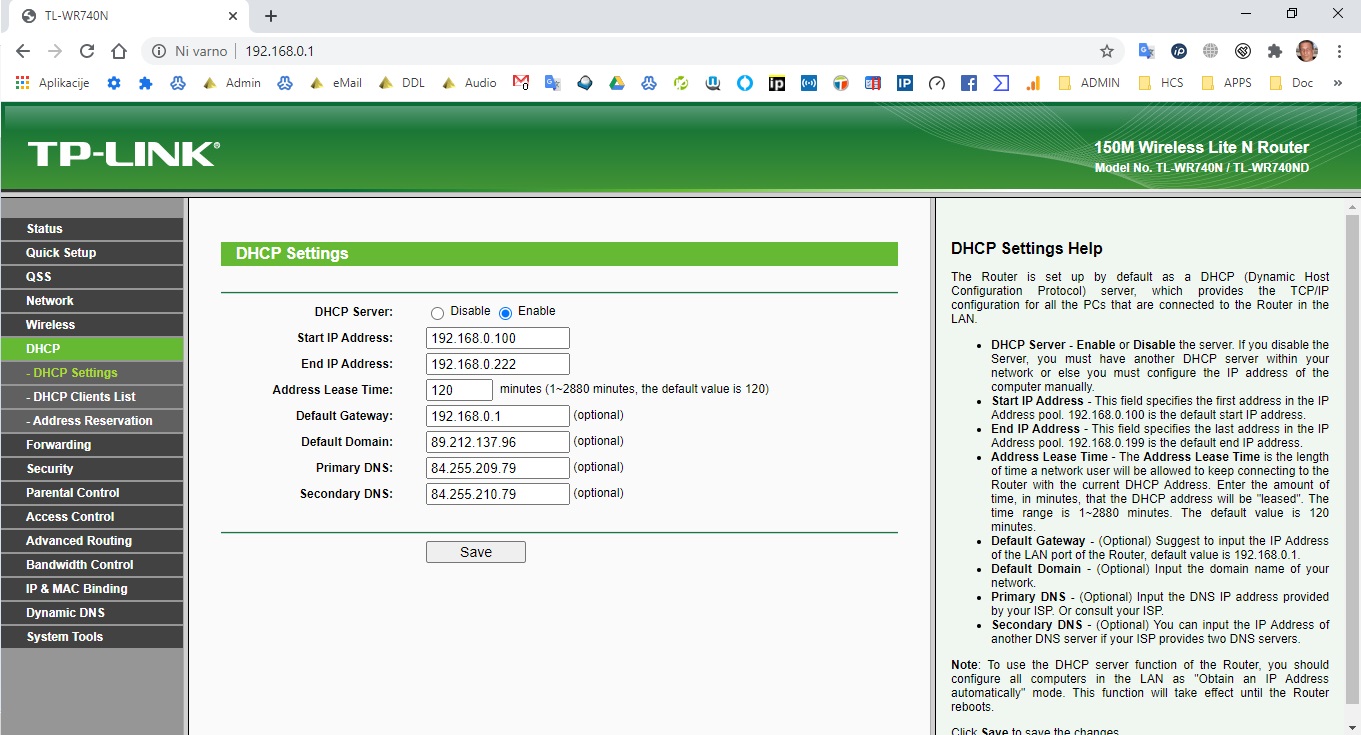

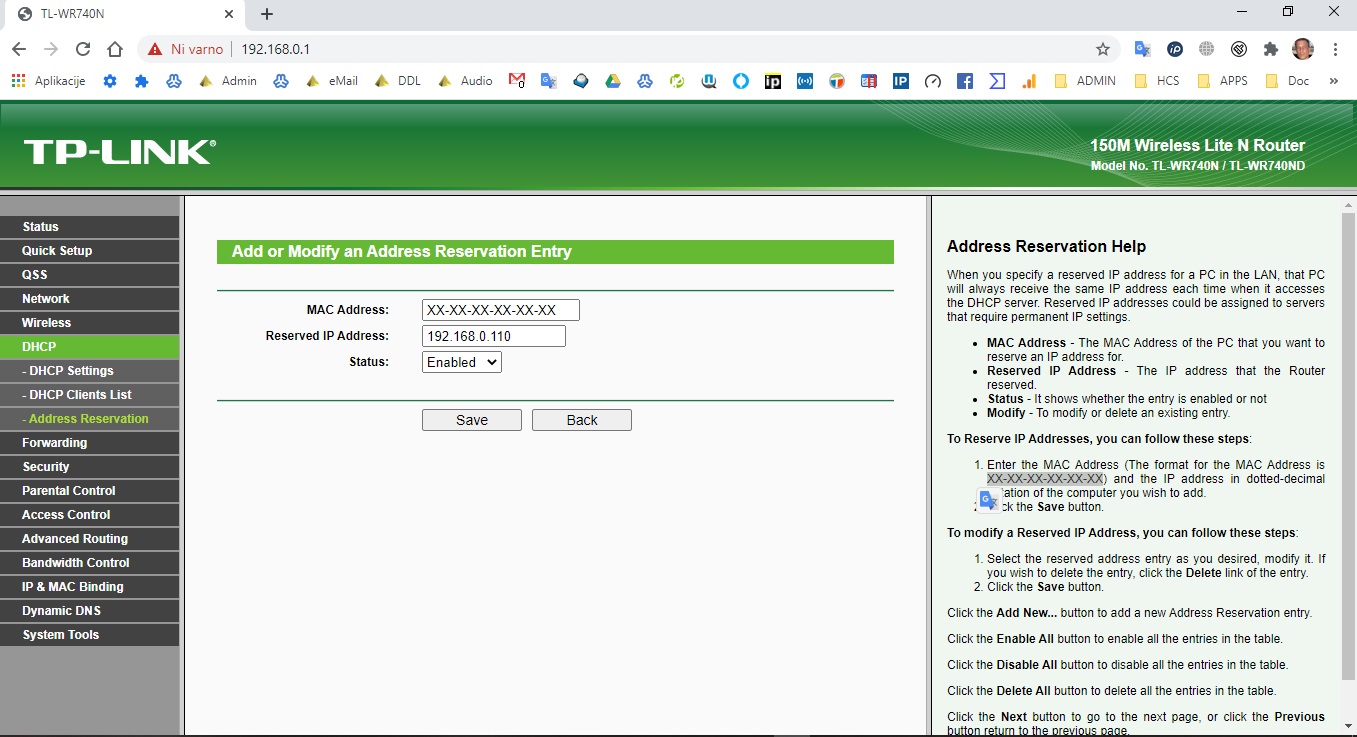
ZDAJ LAHKO ŠE REZERVIRAMO V RASPBERRY PI ZVA VAŠ RASPBIAN LINUX IP, NPR. ČE GA IMATE Z KABLOM POVEZANEGA, ALI WIFI TAKO:
sudo nano /etc/dhcpcd.conf ČE JE PI 4-2-3 POVEZAN S KABLOM KOPIRAJTE SPODNJE DIREKTIVE ČISTO NA KONCU, SE PRAVI 192.168.1.1 JE IP ROUTERJA VI LAHKO IMATE TUDI 192.168.0.1 ODVISNO OD ROUTERJA OZ. USMERJEVALNIKA IN NPR. MOJ PI4 JE NA IPJU 192.168.1.82 – Kopirajte take direktive moj primer:
interface eth0
static ip_address=192.168.1.82/24
static routers=192.168.1.1
static domain_name_servers=192.168.1.1 8.8.8.8 Zdaj, če imate vaš PI preko WiFi povezave pa vpišete tako:
interface wlan0
static ip_address=192.168.1.82/24
static routers=192.168.1.1
static domain_name_servers=192.168.1.1 8.8.8.8 Često na koncu tam kjer je DNS od Google lahko s presledkom ločite še vaš DNS vašega ISP ponudnika npr. t-2.net ima ta dva IP DNS: 84.255.209.79 , 84.255.210.79 medtem, ko za telekom slovenije oz. siol vpišete 193.189.160.13 , 193.189.160.23 in ostali poglejte za vašega ISP!!!
Primer za t-2.net če imate vaš PI preko kabla povezan:
interface eth0
static ip_address=192.168.1.82/24
static routers=192.168.1.1
static domain_name_servers=192.168.1.1 84.255.209.79 84.255.210.79 8.8.8.8 1.1.1.1Za Google DNS sta ta dva 8.8.8.8 in 8.8.4.4 ter za CloudFlare sta ta dva 1.1.1.1 in 1.0.0.1 in poglejte še za Comodo, itd……
06) Ustvari novega uporabnika in izbriši uporabnika pi
V celoti moramo izbrisati obstoječega uporabnika »pi«, ker gre za varnostno težavo. Vsi vemo, da ima Raspberry Pi privzeto uporabniško ime “pi”, zato ga moramo nadomestiti – ZDAJ DOKLER NASTAVLJAMO JE OK PUSTITE AMAPK, NABOLJE JE DA GA IZBRIŠETE.
Če želite ustvariti novega uporabnika, uporabimo ukaz adduser, vendar moramo zagotoviti, da je novi uporabnik v isti skupini kot obstoječi uporabnik pi.
V terminal vnesite:
groups piki bo seznam vseh skupin, v katerih je ta uporabnik se pravi PI. Rezultat bo videti približno tako:
pi adm dialout cdrom sudo audio video plugdev games users netdev inputWe need to create a new user with the same group allocation.
Ustvariti moramo novega uporabnika z enakimi dodelitvami skupin.
Če želite ustvariti novega uporabnika, uporabite ukaz useradd s seznamom vseh kopiranih skupin z zgornjega seznama, skupina pi. V mojem primeru je videti tako, toda vaš bo videti nekoliko drugače:
sudo useradd -m -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,netdev,input <uporabnik>npr. da generiramo uporabnika webscada naredite tako v terminalu:
sudo adduser webscadaIzpolnite Geslo, v terminal geslo kopirate z desnim miškinim kazalcem, pripravite si v namrej dokument oz. TXT datoteko z vašimi gesli in vsemi komandami, ki jih boste potrebovali ali iz te objave kopirajte vse potrebne kode!!!!!
sudo adduser webscada
# MENJAVA GESLA Z:
sudo passwd webscada
#npr. geslo: mojawebscada1234koda
# VEDNO KADAR NPR. IZ TXT DATOTEKE IZ VAŠEGA RAČUNALNIKA KOPIRATE KARKOLI KODO NPT. CTRL+C JO PRILEPITE V TERMINAL Z LEVIM MIŠKINIM KAZALCEM KO KLIKNETE NA TERMINAL NPR. PUTTY ALI SMARTFTP IPD. SSH PROGRAMI OZ. SSH KLIJENT PROGRAMI!!!dodeli webscada previce v terminalu tako, da zažete to komando:
sudo usermod -a -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,input,netdev,spi,i2c,gpio,www-data webscada
# LAHKO TUDI ZA VEČJE ŠTEVILO ADMIN OZ. UPORABNIKOV ČE STE JIH USTVARILI ZA VSAKEGA DAJTE PO ŽELJI DODELITEV PRAVIC, PREMER:
sudo usermod -a -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,input,netdev,spi,i2c,gpio uporabnik1
sudo usermod -a -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,input,netdev,spi,i2c,gpio uporabnik2
sudo usermod -a -G adm,dialout,cdrom,sudo,audio,video,plugdev,games,users,input,netdev,spi,i2c,gpio uporabnik3Zdaj gremo še določit v tem primeru uporabniku webscada, da je s-admin, da vam ne rabi pri komandi sudo su vpisovati gesla ponovno npr. v terminal kopirat kodo z desnim miškinim kazalcem:
sudo nano /etc/sudoers.d/010_pi-nopasswdZdaj vi zamenjajte pi v webscada:
webscada ALL=(ALL) NOPASSWD: ALLZdaj če ste ustvarili večje število uporabnikov in bi želeli, da v terminalu pri izvajanju kode sudo su ne potrebujete vpisati ponovno kode to storite tako:
sudo visudo
root ALL=(ALL) ALL
## na koncu kopirajte npr. tako direktive:
webscada ALL=(ALL) ALL
webscada ALL = NOPASSWD: ALL
### to je že v /etc/sudoers.d/010_pi-nopasswd lahko tudi
### dodate brez problemov še enkrat webscada
uporabnik1 ALL=(ALL) ALL
uporabnik1 ALL = NOPASSWD: ALL
uporabnik2 ALL=(ALL) ALL
uporabnik2 ALL = NOPASSWD: ALL
uporabnik3 ALL=(ALL) ALL
uporabnik3 ALL = NOPASSWD: ALL
# shrani in izhodPonovni zagon in prijava ne več v pi ampak z uporabniškim imenom webscada – Se pravi v Putty ali SmartFTP ali vaš priljubljen program SSH server, se povežete tako, da uporabite uporabniško ime webscada in vaše geslo:
sudo reboot
# Ali s komando ma zgorjna je lažja:
sudo shutdown -r nowBrisanje privzetega uporabnika »pi«
Zdaj lahko uporabnika pi izbrišemo z eno od teh komand sredinska je čisto dovolj zbriše vse datoteke od uporabnika pi:
sudo deluser pi
sudo userdel -r -f pi
sudo deluser -remove-home pi
Izvirnega uporabnika pi in z njim povezane datoteke je treba zdaj izbrisati.
Spremenite podrobnosti o povezavi z oddaljenim namizjem
Ne pozabite spremeniti podrobnosti o povezavi z oddaljenim namizjem, tako da se bo poskušalo prijaviti v novo ime gostitelja in geslo uporabniškega imena se pravi webscada uporabnik in vaše ime gostitelja, ki ste ga spremenili iz raspberry v karkoli.
webscada@hostname-ime-gostitelja-original-je-bilo-raspberrynrp. zdaj ko ste prijavljeni z uporabnikom webscada in npr. ime gostitelja mojascada izgleda tako vaša prijava v terminal:
webscada@mojascada :~ $
ZDAJ BI LAHKO NAMESTILI ŠE NPR. CERTIFIKAT SSH IN GA SKONFIGURIRALI, MA NE RABI, KER NE BOMO POSREDOVALI PORTOV SSH OZ. PORTA 22:
sudo nano /etc/ssh/sshd_configNA KONCU KOPIRAJTE NPR. TAKO:
AllowUsers webscada uporabnik1 uporabnik2 uporabnik3Medtem ko boste SSH ključ generirali če ste terminal zavarovali z SSH certifikatom tako (nastavitve sshd_config) samo za info:
sudo su - webscada
ssh-keygen
sudo su - uporabnik1
sudo su - uporabnik2
ssh-keygen
sudo su - uporabnik3
ssh-keygen
07) Nastavite požarni zid – FireWall linux
Na tej strani oz. poglavju je opisano, kako nastaviti pravila požarnega zidu za blokiranje neželenega prometa na Raspberry Pi.
iptables je krmilnik za netfilter in iptables je vključen v distribucijo Raspberry Pi – Rasbian Linux 10 je derivat Debian Buster 10 Linux. Pozor za tiste, ki nameščate višje različice RPI-10+ se pravi Bullseye Debian 11 oz. raspbian 11 linux, ne pozabit ko ste na začetku nadgradili celoten sistem namestit še iptables / (sudo apt install iptables)
Po meni iptables oz. požarni zid za WEB Scada – Roborina.si
Obstaja več konfiguracijskih sistemov, s katerimi lahko lažje delate z iptables, vendar ne bomo ustvarili veliko pravil, zato bomo lahko ustvarili nabor pravil in nato uvozili nabor pravil v iptables. Pravila, ki jih opisujemo, so posebej za spletni strežnik in vaše zahteve se lahko razlikujejo od tega primera.
Trenutna pravila lahko prikažete z naslednjimi ukazi:
IPv4:
sudo iptables -LIPv6:
sudo ip6tables -Liptables privzeto nima pravil za IPv4 in IPv6, zato boste sprva videli brez pravil požarnega zidu. To pomeni, da je dovoljen ves dohodni, posredovani in odhodni promet – vse je odklenjeno. Dohodni in preusmerjeni promet moramo omejiti le na tisto, kar je potrebno. /(če nimate ipv6 povezave lahko to komot izklopite!!!)
Chain INPUT (policy ACCEPT)
target prot opt source destinationChain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Ustvarjanje nabora pravil požarnega zidu
Kot primer, naslednje ustvarja nabor pravil za IPV4 in IPV6. Primeri so osnovni nabor pravil, ki ga bo morda treba spremeniti glede na vaše posebne sistemske zahteve.
Ustvari novo datoteko v npr. mapi tmp, ki sem jo imenoval V4:
sudo nano /tmp/v4
# Pripravil sem vam tudi že narejeno datoteko za iptables:
/etc/iptables.up.rules PRENESITE IZ TEGA STREŽNIKA IN LAHKO NAMESTO GENERIRAT PRAVILA UPORABITE MOJA SEM VAM VSE ŽE PRIPRAVIL!Kopirajte naslednje oz. spodnje direktive v to datoteko in jo shranite npr. z CTRL+O ali CTRL+X in Shranite Yes – DA za datoteko /tmp/v4!!!. KOPIRAJ SPODNJE DIREKTIVE V SVOJO DATOTEKO /tmp/v4:
# Generated for iptables-webmin-custom-settings by homecraftsoft.com on Mon jul 29 12:06:00 2020
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
# Completed on Mon jul 29 12:06:00 2020
*raw
:PREROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
*mangle
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
# Completed on Mon jul 29 12:06:00 2020
# Generated for iptables-webmin-custom-settings by homecraftsoft.com on Mon jul 29 12:06:00 2020
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT DROP [0:0]
-A INPUT -i lo -j ACCEPT
-A INPUT ! -i lo -d 127.0.0.0/8 -j REJECT
-A INPUT -d 127.0.0.0/8 -j REJECT --reject-with icmp-port-unreachable
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT ! -i eth0 -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags ACK ACK -j ACCEPT
# Accept responses to port 8442 Cybrotech controllers queries
-A INPUT -p udp -m udp --dport 1024:65535 --sport 8442 -j ACCEPT
# Accept responses to our pings
-A INPUT -p icmp -m icmp --icmp-type echo-reply -j ACCEPT
# Accept notifications of unreachable hosts
-A INPUT -p icmp -m icmp --icmp-type destination-unreachable -j ACCEPT
# Accept notifications to reduce sending speed
-A INPUT -p icmp -m icmp --icmp-type source-quench -j ACCEPT
# Accept notifications of lost packets
-A INPUT -p icmp -m icmp --icmp-type time-exceeded -j ACCEPT
# Accept notifications of protocol problems
-A INPUT -p icmp -m icmp --icmp-type parameter-problem -j ACCEPT
# Allow connections to our SSH server
-A INPUT -p tcp -m tcp -m multiport -j ACCEPT --dports ssh,www,https,pop3,smtp,imap,imaps,pop3s,10000,4000,8442
# Allow connections to our IDENT server
-A INPUT -p tcp -m tcp --dport auth -j ACCEPT
# Respond to pings
-A INPUT -p icmp -m icmp --icmp-type echo-request -j ACCEPT
# Protect our NFS server
-A INPUT -p tcp -m tcp --dport 2049:2050 -j DROP
# Protect our X11 display server
-A INPUT -p tcp -m tcp --dport 6000:6063 -j DROP
# Protect our X font server
-A INPUT -p tcp -m tcp --dport 7000:7010 -j DROP
# Allow connections to unprivileged ports
#-A INPUT -p tcp -m tcp --dport 1024:63353 -j ACCEPT
# Accept traceroutes
-A INPUT -p udp -m udp --dport 8442:65535 -j ACCEPT
# Completed on Mon jul 29 12:06:00 2020 Generated for iptables-webmin-custom-settings by homecraftsoft.com on Mon jul 29 12:06:00 2020 Allows all loopback (lo0) traffic and drop all traffic to 127/8 that doesn't use lo0
# WEBMail email ports allow - Spletna poša porti tega ne rabite če ne mislite uporabljat epošte!!!
-A INPUT -p tcp --dport 25 -j ACCEPT
-A INPUT -p tcp --dport 465 -j ACCEPT
-A INPUT -p tcp --dport 587 -j ACCEPT
-A INPUT -p tcp --dport 143 -j ACCEPT
-A INPUT -p tcp --dport 993 -j ACCEPT
-A INPUT -p tcp --dport 110 -j ACCEPT
-A INPUT -p tcp --dport 995 -j ACCEPT
# WEBmin in Cybrotech scgi server
-A INPUT -p tcp --dport 4000 -j ACCEPT
-A INPUT -p tcp --dport 8442 -j ACCEPT
-A INPUT -p tcp --dport 10000 -j ACCEPT
COMMIT
# Completed on Mon jul 29 12:06:00 2020
Ustvari novo datoteko v mapi tmp, ki sem jo imenoval V6:
sudo nano /tmp/v6Kopirajte naslednje v to datoteko in jo shranite – tega ne rabite za Slovenijo:
# Generated for iptables-webmin-custom-settings by homecraftsoft.com on Mon jul 29 12:55:21 2020
*nat
:PREROUTING ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
# Completed on Mon jul 29 12:55:21 2020
*raw
:PREROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
COMMIT
*mangle
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
COMMIT
# Completed on Mon jul 29 12:55:21 2020
# Generated for iptables-webmin-custom-settings by homecraftsoft.com on Mon jul 29 12:55:21 2020
*filter
:FORWARD ACCEPT [0:0]
:INPUT DROP [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -i lo -j ACCEPT
# Dissalow input - connections from outsite localhost
-A INPUT -s ::1/128 ! -i lo -j REJECT
# Accept traffic from internal interfaces
-A INPUT ! -i eth0 -j ACCEPT
# Accept traffic with the ACK flag set
-A INPUT -p tcp -m tcp --tcp-flags ACK ACK -j ACCEPT
# Allow incoming data that is part of a connection we established
-A INPUT -m state --state ESTABLISHED -j ACCEPT
# Allow data that is related to existing connections
-A INPUT -m state --state RELATED -j ACCEPT
# Accept responses to DNS queries UPD connedtion port ipv4 8442 open all ports from 1024 to 65535
-A INPUT -p udp -m udp --dport 1024:65535 --sport 8442 -j ACCEPT
#-A INPUT -p udp -m udp --dport 1024:65535 --sport 8442 -j ACCEPT
-A INPUT -p tcp -m tcp -m multiport -j ACCEPT --dports ftp,ssh,www,https,pop3,smtp,imap,imaps,pop3s,8338,4000,10000
## Allow connections to our IDENT server
-A INPUT -p tcp -m tcp --dport auth -j ACCEPT
# Respond to pings -A INPUT -p icmp -m icmp --icmp-type echo-request -j ACCEPT Protect our NFS server
-A INPUT -p tcp -m tcp --dport 2049:2050 -j DROP
# Protect our X11 display server
-A INPUT -p tcp -m tcp --dport 6000:6063 -j DROP
# Protect our X font server
-A INPUT -p tcp -m tcp --dport 7000:7010 -j DROP
-A INPUT -j REJECT
-A FORWARD -j REJECT
COMMIT
# Completed IPTables Custom Config
Naložite iptable pravila
Za nalaganje iptable uporabljamo ukaze:
sudo iptables-restore < /tmp/v4
sudo ip6tables-restore < /tmp/v6
Potrebujemo način, da zagotovimo, da so pravila iptable na voljo po ponovnem zagonu, zato moramo namestiti iptables-persistent z uporabo:
sudo apt-get install iptables-persistent ipsetVprašani boste, ali želite shraniti trenutna pravila IPv4 in IPv6. Na vsak poziv odgovorite z da – YES!!!.
Če želite, lahko odstranite začasni datoteki v4 in v6.
Pravila požarnega zidu lahko ponovno preverimo z uporabo komande:
sudo iptables -vL
sudo ip6tables -vL
To so osnovna pravila požarnega zidu. Vendar boste morda morali ta pravila urediti, če se namestitev na primer spremeni v datoteki strežnika.
VSE GLEDE IPTABLES SE PRAVI LINUX POŽARNEGA ZIDU BOSTE DOBILI NA STRANI DEBIAN VSE DIREKTIVE VELJAJO TUDI ZA RASBIAN!!!
https://www.debian.org/
PS: SORRY AMPAK JAZ PIŠEM VSE MOJE PROGRAME V ANGLEŠČINI IN TO VELJA TUDI ZA RAZLAGE TAKO DA BREZ ZAMERE – PRI RAZVOJU LASTNIH SPLETNIH APLIKACIJ MI POMAGAJO PRIJATELJI IZ TUJINE TAKO DA NE MOREM PISATI V SLOVENŠČINI NOBENE RAZLAGE, KONEC KONCEV JE STANDARDNI JEZIK ZA ITS ZAME ANGLEŠČINA, ŠE WINDOWSA IN NOBENEGA PROGRAMA NIMAM V SL-SI SLOVENSKEM JEZIKU STVAR NAVADE.
PRENESITE SI MOJE IPTABLES IZKLJUČNO ZA RASPBERRY PI, KI SEM JIH PRIPRAVIL ZA VAS UPORABNIKE PCSNET OZ. HTU IN UITW ORG. EU PREKO TEGA URL – https://perc.ddns.net/ddl/download.php:

sudo nano /etc/iptables.up.rulesKopirajte vse direktive iz moje datoteke iptables.up.rules ki ste jo prenesli in odzipali na vaš računalnik ter to velja še za:
sudo nano /etc/ip6tables.up.rulesKopirajte direktive iz moje datoteke za ip6tables.up.rules in namestite tako:
sudo iptables-restore < /etc/iptables.up.rules
sudo ip6tables-restore < /etc/ip6tables.up.rules
sudo apt-get install iptables-persistent -y
sudo reboot
sudo iptables -vL
sudo ip6tables -vLwebscada@mojascada:~ $ sudo iptables -vL
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
216K 163M ACCEPT all — lo any anywhere anywhere
0 0 REJECT all — !lo any anywhere 127.0.0.0/8 reject-with icmp-port-unreachable
0 0 REJECT all — any any anywhere 127.0.0.0/8 reject-with icmp-port-unreachable
142K 65M ACCEPT all — any any anywhere anywhere state RELATED,ESTABLISHED
0 0 ACCEPT all — any any anywhere anywhere ctstate RELATED,ESTABLISHED
0 0 ACCEPT all — !eth0 any anywhere anywhere
0 0 ACCEPT tcp — any any anywhere anywhere tcp flags:ACK/ACK
1178 68660 ACCEPT tcp — any any anywhere anywhere ctstate NEW,ESTABLISHED tcp dpt:http
0 0 ACCEPT tcp — any any anywhere anywhere ctstate NEW,ESTABLISHED tcp dpt:https
itd….. IZPIŠE SE VAM KOMPLET KONFIGURACIJA POŽARNEGA ZIDU
Chain OUTPUT (policy ACCEPT 1239 packets, 124K bytes)
pkts bytes target prot opt in out source destination
webscada@mojascada:~ $
8) Namestite Apache2 na Raspberry Pi
Namestitev spletnega strežnika Apache na Raspberry Pi mora biti neposredna. To predpostavlja, da ste za Raspberry Pi nastavili ime gostitelja in da je povezani z vašim lokalnim omrežjem.
Prijavite se na Raspberry Pi s pomočjo terminala in vnesite:
sudo apt update
# ali kar to spodaj direktivo kopirajte v terminal:
sudo apt update && sudo apt upgrade -y
Namestitev Apache 2 strežnika:
sudo apt-get install apache2 -y
# ali s to komando še za pripomočke:
sudo apt-get install apache2 apache2-utils -yPreizkusite spletni strežnik
Apache privzeto postavi preskusno datoteko HTML v spletno mapo, ki si jo boste lahko ogledali iz svojega Pi ali iz drugega računalnika v omrežju.
Odprite privzeto spletno stran Apache na Raspberry Pi s pomočjo spletnega brskalnika na Raspberry Pi in vnesite http://mojascada oz. vaše ime gostitelja ki ste ga določili (raspberry npr. webscada@mojascada :~ $)
Videti bi morali privzeto stran Apache2 Debian.
Poskusite namesto localhost PI, ki ste ga določiti uporabiti kar IP za Raspberry Pi vaše lokalno omrežje. Na primer, moje ime gostitelja je mojascada, zato namesto tega bom uporabil http://ipraspberry v mojem primeru je http://192.168.1.82.
Lahko v vaše spletnem brskalniku uporabite ali eno ali drugo po želji.
Če želite poiskati naslov IP vašega Raspberry Pi, v terminal vnesite naslednje:
hostname -ISpreminjanje privzete spletne strani
Privzeta spletna stran je samo datoteka HTML v datotečnem sistemu. Nahaja se na /var/www/html/index.html.
Če želite spremeniti to datoteko:
sudo nano /var/www/html/index.htmlVendar mi tega ne potrebujemo zato jo lahko kar izbrišemo tako:
cd /var/www/html/
webscada@mojascada:/var/www/html $
## in za ibris te datoteke ali vse zažkite to komando:
# IZBRIS INDEX.HTML APACHE
sudo rm *Če želite kadar koli znova zagnati Apache, vnesite:
Zdaj gremo skonfigurirat Apache2 za WEBScado tako da v terminalu zažegmo to direktivo:
sudo nano /etc/apache2/apache2.confdodajte še kakšen virtualni host po želji npr. pod direktivo /var/www kopirajte pot vaše druge aplikacije:
<Directory /var/www/html/>
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>ZA PREVERIT ČE DELA APACHE ODPRI V BRSKALNIKU URL:
http://IPLocalPI4/
Če ne deluje v terminalu uporabi kodo:
sudo chown -R www-data:www-data /var/www/html/Ter čiso na koncu kopirajte to direktivo spodaj vse od alineje 228 v apache.conf dodaj localhost ime strežnika in pol ko namestite in popravite vse py datoteke za scada kopirate še v to datoteko solar cybro – PS jaz bi rajši te iste direktive apache.conf od robotina .si kopiral v vHosts se pravi 000-default.conf apache konfiguracija za virtualne hoste:
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
ServerName localhost
## WEBSCADA KO SE NAMESTI SE VKLJUČI SPODNJE DIREKTIVE:
# solar cybro web application static files directory
Alias /static/ /home/webscada/app/solar_cybro/static/
<directory "/home/webscada/app/solar_cybro/static/">
# Order deny,allow
Require all granted
</directory>
# solar cybro web application data directory
Alias /data/ /home/webscada/app/solar_cybro/data/
<directory "/home/webscada/app/solar_cybro/data/">
# Order deny,allow
Require all granted
</directory>
# location of solar cybro wsgi startup file
WSGIScriptAlias / /home/webscada/app/solar_cybro/solar_cybro.wsgi
<directory "/home/webscada/app/solar_cybro/">
# Order deny,allow
Require all granted
</directory>
## Te direktive rabijo za scado - shranite datoteko
Lahko pa te iste direktive zgoraj v apache.conf dodate v vaš virtual hostse pravi za mapo /var/www/html/ doličite pot webscada in izbrišete to iz apache.conf primer 000-defaul.conf to je moj osebni način s to razliko da se naredi en nebulozni host za vaš fiksni ip pred tem hostom spodaj, npr. date server name vaš ip in določite v apache.conf ter 000-default.conf mapo za nebulozni host npr. /var/www/null/ ter ustvarite nek html ali php dokument:
<VirtualHost *:80>
ServerName mojadomena.noip.com
#DocumentRoot /var/www/html
#<Directory /var/www/html/>
#Options Indexes FollowSymLinks MultiViews
#AllowOverride All
#Require all granted
#</Directory>
# solar cybro web application static files directory
Alias /static/ /home/webscada/app/solar_cybro/static/
<directory “/home/webscada/app/solar_cybro/static/”>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Require all granted
</directory>
# solar cybro web application data directory
Alias /data/ /home/webscada/app/solar_cybro/data/
<directory “/home/webscada/app/solar_cybro/data/”>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Require all granted
</directory>
# location of solar cybro wsgi startup file
WSGIScriptAlias / /home/webscada/app/solar_cybro/solar_cybro.wsgi
<directory “/home/webscada/app/solar_cybro/”>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Require all granted
</directory>
ErrorLog /var/log/apache2/error.log
CustomLog /var/log/apache2/access.log combined
# Enable RewriteEngine
RewriteEngine On
# Recommended: XSS protection
<IfModule mod_headers.c>
Header set X-XSS-Protection “1; mode=block”
Header always append X-Frame-Options SAMEORIGIN
Header set X-Content-Type-Options: “nosniff”
</IfModule>
# Disable HTTP 1.0 Protocol
# RewriteEngine On
RewriteCond %{THE_REQUEST} !HTTP/1.1$
RewriteRule .* – [F]
</VirtualHost>
9) Namestite php 7.4 PI 4-3-2
Zdaj bomo namestili in dali v repository oz. bazo podatkov za nadgradno skriptov php različica 7.4 nekaj direktiv.
V putty oz. terminalu vnesite spodnje direktive:
sudo apt update
sudo apt -y install lsb-release apt-transport-https ca-certificates
sudo wget -O /etc/apt/trusted.gpg.d/php.gpg https://packages.sury.org/php/apt.gpg
echo "deb https://packages.sury.org/php/ $(lsb_release -sc) main" | sudo tee /etc/apt/sources.list.d/php.list
sudo apt update
sudo apt -y install php7.4 libapache2-mod-php7.4
# preverite različico s to komando:
php -v
## urejanje direktiv php
webscada@mojascada:~ $ sudo nano /etc/php/7.4/apache2/php.ini
sudo nano /etc/php/7.4/apache2/php.ini
# vpišite po želji vrednosti se pravi:
max_execution_time = 60
memory_limit = 128M
post_max_size = 128M
upload_max_filesize = 128M
max_execution_time = 600
max_input_vars = 3000
max_input_time = 1000
log_errors = On
error_log = /var/log/php/error.logZdaj moramo še ustvarit mapo za napake, v terminalu zažgete spodnji komandi:
sudo mkdir -p /var/log/php
sudo chown www-data /var/log/phpZdaj module za php 7.4 namestite tako:
sudo apt install php7.4-{common,mysql,cgi,xml,xmlrpc,curl,gd,imagick,cli,dev,imap,mbstring,opcache,soap,zip,intl,bcmath} -y
# ali tako:
sudo apt install -y php7.4-fpm php7.4-mysql php7.4-dom php7.4-simplexml php7.4-ssh2 php7.4-xml php7.4-xmlreader php7.4-curl php7.4-exif php7.4-ftp php7.4-gd php7.4-iconv php7.4-imagick php7.4-json php7.4-mbstring php7.4-posix php7.4-sockets php7.4-tokenizerZdaj za WEBMin če želite gledati slike namestite še to:
sudo apt-get install imagemagick php-imagick libmagickcore-dev -yWEB SCADA potrebuje spodnje module php in serverje Debian 10 / 11:
# sudo apt install apache2 mariadb-server mariadb-client php phpmyadmin libapache2-mod-wsgi acl ssh -y
sudo apt install libapache2-mod-wsgi acl ssh -y
sudo apt install python-django python-pip python-mysqldb -y
# WEB SCADA POTREBUJE TE MOUDLE PHP:
sudo apt install libapache2-mod-php7.4 php7.4-json php7.4-fpm php7.4-cli -y
## Se pravi za php 7.4 lahko namestite tako samo te ki rabite ločite z vejico je krajša komanda:
sudo apt install php7.4-{common,mysql,cgi,xml,fpm,curl,gd,imagick,cli,dev,imap,mbstring,opcache,soap,zip,json} -y
# Za vklopit npr. modul apache rewrite in mysqli:
##sudo phpenmod mysqli
sudo a2enmod rewrite
# in spodnja za ponovno zagnat apache:
sudo systemctl restart apache2
sudo service apache2 restart10) Namestite SQL server
Namestitev SQL sever zdaj ta najnovejši se imenuje MariaDB
V putty oz. terminalu vnesite spodnje direktive:
sudo apt-get install mariadb-client mariadb-server -y
Skonfiguriraj MariaDB na SSL:
sudo su
cd /etc/mysql
sudo mkdir ssl
cd ssl
4096 ali / or - 2048 je ok
sudo openssl genrsa 2048 > ca-key.pem
Naredimo SSL za Admin MySQL: sudo openssl req -new -x509 -nodes -days 999000 -key ca-key.pem -out ca-cert.pem
Izpolni SI, itd in za Common Name daj to:
Common Name (e.g. server FQDN or YOUR name) []: MariaDB admin
Naredimo SSL za Server MySQL: sudo openssl req -newkey rsa:2048 -days 999000 -nodes -keyout server-key.pem -out server-req.pem
Izpolni SI, itd in za Common Name daj to:
Common Name (e.g. server FQDN or YOUR name) []: MariaDB server
Naredimo SSL za Server MySQL: sudo openssl req -newkey rsa:2048 -days 999000 -nodes -keyout client-key.pem -out client-req.pem
Izpolni SI, itd in za Common Name daj to: Common Name (e.g. server FQDN or YOUR name) []: MariaDB client
Zdaj preveri če so vsi certifikati ok: sudo openssl rsa -in server-key.pem -out server-key.pem sudo openssl x509 -req -in server-req.pem -days 999000 -CA ca-cert.pem -CAkey ca-key.pem -set_serial 01 -out server-cert.pem sudo openssl rsa -in client-key.pem -out client-key.pem sudo openssl x509 -req -in client-req.pem -days 999000 -CA ca-cert.pem -CAkey ca-key.pem -set_serial 01 -out client-cert.pem openssl verify -CAfile ca-cert.pem server-cert.pem client-cert.pem
Aktiviraj v SQL SSL: sudo nano /etc/mysql/mariadb.conf.d/50-server.cnf
## Dodaj v sekciji [mysqld] spodnje direktive: ## mariadb will use TLSv1.0 or better. ## ssl = on ssl-ca=/etc/mysql/ssl/ca-cert.pem ssl-cert=/etc/mysql/ssl/server-cert.pem ssl-key=/etc/mysql/ssl/server-key.pem
Dodeli pooblastila: sudo chown -Rv mysql:root /etc/mysql/ssl/ sudo systemctl restart mysql
ZDAJ ŠE V MYSQL CLIENTS DODAJ V SEKCIJI [mysql] SPODNJE DIREKTIVE:
sudo nano /etc/mysql/mariadb.conf.d/50-mysql-clients.cnf
## MySQL Client Configuration ##ssl-ca=/etc/mysql/ssl/ca-cert.pemssl-cert=/etc/mysql/ssl/client-cert.pemssl-key=/etc/mysql/ssl/client-key.pem
zDAJ KOPIRAJTE VSAKEMU KLIJENTU VAŠ SSL CERTIFIKAT OZ. VAŠIM RAČUNOM:
{admin@mojserver}: rsync /etc/mysql/ssl/ca-cert.pem /etc/mysql/ssl/client-cert.pem /etc/mysql/ssl/client-key.pem \admin@localhost:/etc/mysql/ssl
Vpiši svojo kodo in tako naredi za vsak račun npr.
rsync /etc/mysql/ssl/ca-cert.pem /etc/mysql/ssl/client-cert.pem /etc/mysql/ssl/client-key.pem \webscada@localhost:/etc/mysql/ssl
pojdi preverit če vse dela sudo su in mariadb:
mariadb
Welcome to the MariaDB monitor. Commands end with ; or \g.Your MariaDB connection id is 30Server version: 10.5.15-MariaDB-0+deb11u1 Raspbian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> SHOW VARIABLES LIKE '%ssl%';+---------------------+--------------------------------+| Variable_name | Value |+---------------------+--------------------------------+| have_openssl | YES || have_ssl | YES || ssl_ca | /etc/mysql/ssl/ca-cert.pem || ssl_capath | || ssl_cert | /etc/mysql/ssl/server-cert.pem || ssl_cipher | || ssl_crl | || ssl_crlpath | || ssl_key | /etc/mysql/ssl/server-key.pem || version_ssl_library | OpenSSL 1.1.1n 15 Mar 2022 |+---------------------+--------------------------------+10 rows in set (0.006 sec)
MariaDB [(none)]> status;--------------mariadb Ver 15.1 Distrib 10.5.15-MariaDB, for debian-linux-gnueabihf (armv8l) using EditLine wrapper
Connection id: 30Current database:Current user: root@localhostSSL: Cipher in use is TLS_AES_256_GCM_SHA384Current pager: stdoutUsing outfile: ''Using delimiter: ;Server: MariaDBServer version: 10.5.15-MariaDB-0+deb11u1 Raspbian 11Protocol version: 10Connection: Localhost via UNIX socketServer characterset: utf8mb4Db characterset: utf8mb4Client characterset: utf8Conn. characterset: utf8UNIX socket: /run/mysqld/mysqld.sockUptime: 3 min 43 sec
Threads: 1 Questions: 60 Slow queries: 0 Opens: 32 Open tables: 25 Queries per second avg: 0.269--------------
MariaDB [(none)]> quitBye
11) Namestite phpmyadmin
Namestitev phpmyadmin, bomo potrebovali ta program za lažji uvoz SQL baz podatkov ali pa redne varnostne kopije SQL baze podatkov ma vse to vam bo delal WEBMin!!! PhpMyAdmin potrebuje webscada pridemo do tega še….
V putty oz. terminalu vnesite spodnje direktive:
sudo apt-get install phpmyadmin -yZdaj vas vpraša ko se namešča program za uporabniško ime phpmyadmin da določite eno kodo, dajte npr. nekaj hard oz. težjo kodo vse to si zapišite!
Npr. pri namestitvi phpmyadmin vas vpraša za kodo uporabnik:
phpmyadmin
npr. koda dajte kaj tazga, to velja vedno tudi za sql bazo ali pa še posebej npr. za uporabnika webscada naj bo kompleksna koda!!!
Koda za phpmyadmin: 4R4pESMaZbkcvN79kR3K4BeK
Ni pa nujno po želji določite eno kodo!!!Zdaj se lahko prijavimo v phpmyadmin tako, da odpremo v brskalniku:
http://192.168.1.82/phpmyadmin/
### se pravi vaš ip raspberry!!!Če so neki hrošči za popravit poglejte npr. google.com in napišite oz. kopirajte uno napako št. tukaj vam pokažem kako odpravit en hrošč, vendar boste ni pa potrebno mogli še za neke fonte oz pisavo popravit hrošče oz. bugs jaz pravim, boste mogli DEBUGIZIRAT oz. RAZHROŠČIT SKRIŠTE TAKO: NE RABI VEČ POPRAVLJAT V RASBIAN LINX 11 !!!!! SE UPORABLJA PO DEFAULTU POPRAVLJENA VERZIJA 5.0.4
sudo nano +551 /usr/share/phpmyadmin/libraries/plugin_interface.lib.phpPopravite alinejo ki se glasi tako:
if ($options != null && count($options) > 0) {spremenite tako, da izgleda tako:
if ($options != null && count((array)$options) > 0) {Pol so še hrošči kot sem reku za neke fonte oz. pisave, ma ni to pomembo, glejte github.com spletno mesto so vsi popravki hroščev za phpmyadmin, ni težko mislim če se pravilno spomnim da je za popravit v mapi, /usr/share/php/tcpdf/tcpdf.php v alineji 1963:
sudo nano +1963 /usr/share/php/tcpdf/tcpdf.php
TCPDF_FONTS::utf8Bidi(array(''), '', false, $this->isunicode, $this->CurrentFont);popravite tako oz. debugizirate odpravite hrošča z:
TCPDF_FONTS::utf8Bidi(array(), '', false, $this->isunicode, $this->CurrentFont); Posodobite phpmyadmin na npr. 5.0.4 na najnovejšo verzijo
Posodobite phpmyadmin na npr. 5.0.4 na najnovejšo verzijo
cd /usr/share/phpmyadmin/sudo su
wget https://perc.ddns.net/ddl/phpMyAdmin.zip
unzip phpMyAdmin.ziprm phpMyAdmin.zip
sudo cp /usr/share/phpmyadmin/config.sample.inc.php /usr/share/phpmyadmin/config.inc.php
sudo nano /usr/share/phpmyadmin/config.inc.php
$cfg['blowfish_secret'] = 'VPIŠI-SVOJO-KODO-ZAKODIRAT-COOKY'; /* YOU MUST FILL IN THIS FOR COOKIE AUTH! *//* User used to manipulate with storage */// $cfg['Servers'][$i]['controlhost'] = '';// $cfg['Servers'][$i]['controlport'] = '';$cfg['Servers'][$i]['controluser'] = 'pma';$cfg['Servers'][$i]['controlpass'] = 'MOJSERVER123456789';/* Storage database and tables */$cfg['Servers'][$i]['pmadb'] = 'phpmyadmin';$cfg['Servers'][$i]['bookmarktable'] = 'pma__bookmark';$cfg['Servers'][$i]['relation'] = 'pma__relation';$cfg['Servers'][$i]['table_info'] = 'pma__table_info';$cfg['Servers'][$i]['table_coords'] = 'pma__table_coords';$cfg['Servers'][$i]['pdf_pages'] = 'pma__pdf_pages';$cfg['Servers'][$i]['column_info'] = 'pma__column_info';$cfg['Servers'][$i]['history'] = 'pma__history';$cfg['Servers'][$i]['table_uiprefs'] = 'pma__table_uiprefs';$cfg['Servers'][$i]['tracking'] = 'pma__tracking';$cfg['Servers'][$i]['userconfig'] = 'pma__userconfig';$cfg['Servers'][$i]['recent'] = 'pma__recent';$cfg['Servers'][$i]['favorite'] = 'pma__favorite';$cfg['Servers'][$i]['users'] = 'pma__users';$cfg['Servers'][$i]['usergroups'] = 'pma__usergroups';$cfg['Servers'][$i]['navigationhiding'] = 'pma__navigationhiding';$cfg['Servers'][$i]['savedsearches'] = 'pma__savedsearches';$cfg['Servers'][$i]['central_columns'] = 'pma__central_columns';$cfg['Servers'][$i]['designer_settings'] = 'pma__designer_settings';$cfg['Servers'][$i]['export_templates'] = 'pma__export_templates';
$cfg['TempDir'] = '/var/lib/phpmyadmin/tmp';$cfg['SaveDir'] = '/var/lib/phpmyadmin/doc';$cfg['UploadDir'] = '/var/lib/phpmyadmin/ddl';
Shrani in ustvari mape ter jim dodeli dkupino in uporabnika:
sudo mkdir /var/lib/phpmyadmin/tmpsudo mkdir /var/lib/phpmyadmin/docsudo mkdir /var/lib/phpmyadmin/ddl
sudo chown -R www-data:www-data /var/lib/phpmyadmin/tmpsudo chown -R www-data:www-data /var/lib/phpmyadmin/docsudo chown -R www-data:www-data /var/lib/phpmyadmin/ddl
Instaliraj password generator da maš pol kode vedno za karkoli tako:
sudo apt install pwgen
Kodo generiraš npr. eno kodo od 32 mest tako:
pwgen -s 32 1
#phpmyadmin upgrade – update new version: Gremo dalje ko si uno gor naredu zdaj obvezno tako:
sudo mariadb < /usr/share/phpmyadmin/sql/create_tables.sql
sudo mariadb
GRANT SELECT, INSERT, UPDATE, DELETE ON pma_db.* TO ‘pma’@’localhost’ IDENTIFIED BY ‘MOJSERVER123456789’;
GRANT SELECT, INSERT, UPDATE, DELETE ON phpmyadmin.* TO ‘pma’@’localhost’ IDENTIFIED BY ‘MOJSERVER123456789’;
GRANT ALL PRIVILEGES ON *.* TO ‘phpmyadmin’@’localhost’ WITH GRANT OPTION;
FLUSH PRIVILEGES;
GRANT ALL PRIVILEGES ON *.* TO ‘admin’@’localhost’ IDENTIFIED BY ‘SudoKodaAdministratorjaSQL’ WITH GRANT OPTION;
FLUSH PRIVILEGES;
prijavite se v phpmyadmin http://serverip/phpmyadmin/
admin
SudoKodaAdministratorjaSQL
12) Namestite WEBSCADA CybroTech Kontrolerji
Recimo da ste ustvarli xy uporabnika lahko direktno poberete iz mojega mesta app in samo menjate poti serverja v nastavitvah za vašega uporabnika scada:
cd /home/webscada/wget https://perc.ddns.net/ddl/app.zipunzip app.zipsudo setfacl -m u:www-data:--x /home/webscada/appsudo setfacl -R -m u:www-data:--- /home/webscada/app/*sudo setfacl -R -m u:www-data:rwx /home/webscada/appsudo setfacl -R -m d:u:www-data:rwx /home/webscada/appsudo chmod g+s /home/webscada/appsudo setfacl -R -m d:u:webscada:rwx /home/webscada/appsudo chmod 755 /home/webscada/app/scgi_server/src/cybro_com_server.pysudo chmod 755 /home/webscada/app/scgi_server/src/cybro_scgi_server.pysudo chmod 755 /home/webscada/app/scgi_server/src/run_scgi_server.pyapp/scgi_server/src/cybro_scgi_server.py start
Prvo si prenesemo WEBScado na naš račun oz. uporabnika webscada www.cybrotech.com:
wget http://www.cybrotech.com/wp-content/uploads/2019/04/CyBroWebScada-v1.1.10-v2.3.0.zipZdaj jo odpakirajte z direktivo:
unzip CyBroWebScada-v1.1.10-v2.3.0.zipKot sem že napisal scada rabi sledeče module:
# WEB Scada rabi spodnje serverje in apps Debian 10 Raspbian 10 Ubuntu14-18:
sudo apt install apache2 mariadb-server mariadb-client php7.4 phpmyadmin libapache2-mod-wsgi acl ssh -y
# POZOR python django apps (Scada novejši django apps so različico 3.1 NE deluje, za CybroTech WEB Scado.. to rezličico uporabite sudo pip install django==1.3
sudo apt install python-django python-pip python-mysqldb -y
sudo apt install libapache2-mod-php7.4 php7.4-json php7.4-fpm php7.4-cli libapache2-mod-wsgi acl ssh -y
# Potrebna programska oprema za WEB Scada Ubuntu:
$ sudo apt-get install apache2 mysql-server php5 phpmyadmin libapache2-mod-wsgi acl ssh
$ sudo apt-get install python-pip python-mysqldb
$ sudo pip install django==1.3
$ sudo pip install pytz
$ sudo apt-get install python-dev python-setuptools
$ sudo apt-get install libjpeg-dev zlib1g-dev
$ sudo pip install pillow
$ sudo apt-get install apache2 mariadb-server php phpmyadmin libapache2-mod-wsgi acl ssh
$ sudo apt-get install python-django python-pip python-mysqldb
Zdaj gremo še v avtomatični zagon programov in kopiramo spodnje direktive:
sudo nano /etc/rc.local
# KOPIRAJTE TO TAKO:
# rc.local
sudo -u webscada /home/webscada/app/scgi_server/src/run_scgi_server.py
# sudo noip2
# sudo ufw enable
#
# This script is executed at the end of each multiuser runlevel.IN LAHKOŠE CRON JOBS OZ. CRON TABLES DATE TO DIREKTIVO TAKO:
crontab -e
# KOPIRAJTE NA KONCU DA SE SAMODEJNO ZAŽENE WSCGI STREŽNIK:
*/1 * * * * /home/webscada/app/scgi_server/src/run_scgi_server.py &>/dev/null
*/10 * * * * /home/webscada/app/solar_cybro/project/run_create_reports.py &>/dev/null
*/2 * * * * /home/webscada/app/solar_cybro/project/run_send_reports.py &>/dev/null
# PONOVNI ZAGON APACHE TAKO:
sudo service apache2 restart
# ali
sudo apachectl -k restartZdaj zaženemo se ti dve komandi v terminalu npr. putty:
cd /home/webscada
setfacl -m u:www-data:--x /home/webscadasetfacl -R -m u:www-data:--- /home/webscada/app/*setfacl -R -m u:www-data:rwx /home/webscada/appsetfacl -R -m d:u:www-data:rwx /home/webscada/appchmod g+s /home/webscada/appsetfacl -R -m d:u:webscada:rwx /home/webscada/app
sudo setfacl -m u:www-data:--x $HOME && sudo setfacl -R -m u:www-data:--- $HOME/app/* && sudo setfacl -R -m u:www-data:rwx $HOME/app && sudo setfacl -R -m d:u:www-data:rwx $HOME/app && sudo chmod g+s $HOME/app && sudo setfacl -R -m d:u:webscada:rwx $HOME/app
sudo chmod 755 app/scgi_server/src/cybro_com_server.py && sudo chmod 755 app/scgi_server/src/cybro_scgi_server.py && sudo chmod 755 app/scgi_server/src/run_scgi_server.py
# Daljša varianta kopirajte vse skupaj v terminal:
sudo setfacl -m u:www-data:--x $HOME
sudo setfacl -R -m u:www-data:--- $HOME/app/*
sudo setfacl -R -m u:www-data:rwx $HOME/app
sudo setfacl -R -m d:u:www-data:rwx $HOME/app
sudo chmod g+s $HOME/app
sudo setfacl -R -m d:u:webscada:rwx $HOME/app
# Spremenite pooblastila datotekam:
sudo chmod 755 app/scgi_server/src/cybro_com_server.py
sudo chmod 755 app/scgi_server/src/cybro_scgi_server.py
sudo chmod 755 app/scgi_server/src/run_scgi_server.py
sudo service apache2 restart
# Lahko krajša varianta za pooblastila:
sudo setfacl -m u:www-data:--x $HOME && sudo setfacl -R -m u:www-data:--- $HOME/app/* && sudo setfacl -R -m u:www-data:rwx $HOME/app && sudo setfacl -R -m d:u:www-data:rwx $HOME/app && sudo chmod g+s $HOME/app && sudo setfacl -R -m d:u:webscada:rwx $HOME/app
sudo chmod 755 app/scgi_server/src/cybro_com_server.py && sudo chmod 755 app/scgi_server/src/cybro_scgi_server.py && sudo chmod 755 app/scgi_server/src/run_scgi_server.py
Zdaj npr. če naredite takšno bazo podatkov za SQL kot bom jaz in seveda ste prijavljeni v terminal z uporabnikom webscada:
sudo nano /home/webscada/app/solar_cybro/project/settings_local.pyDatoteka izgleda tako, jaz sem ustvaril SQL bazo podatkov za scado tako da je baza SQL pod imenom bazasolar in uporabnik webscada – vi lahko to po želji kakor vam paše to bomo generirali bazo in uporabnika v naslednjem poglavju, če boste dodelili drugo to tudi primerno spremenite:
# -*- coding: utf-8 -*-
import version
ADMINS = (
('Cybrotech', 'info@cybrotech.hr'),
)
DATABASE_ENGINE = 'mysql' # 'postgresql_psycopg2', 'postgresql', 'mysql', 'sqlite3' or 'oracle'.
DATABASE_NAME = 'scada' # Or path to database file if using sqlite3.
DATABASE_USER = 'scada' # Not used with sqlite3.
DATABASE_PASSWORD = 'p90k7VOEaLppRx2a' # Not used with sqlite3.
DATABASE_HOST = 'localhost' # Set to empty string for localhost. Not used with sqlite3.
DATABASE_PORT = '3306' # Set to empty string for default. Not used with sqlite3.
SMTP_HOST = 'smtp.dummy.com'
SMTP_HOST_USER = 'solar_noreply'
SMTP_HOST_PASSWORD = ''
SMTP_PORT = 25
SMTP_USE_TLS = False
DEFAULT_FROM_EMAIL = "noreply@..." # from address for server error emails
SERVER_EMAIL = "noreply@..." # used as the from address for django.core.mail.mail_admins() and django.core.mail.mail_managers()
TIME_ZONE = 'Europe/Zagreb'
SECRET_KEY = "$$|Y6_0f]6$1&^8Wv4673;J%JR-b%ln@iV6?AhI.5,t?>`kS"
REPORT_FROM_EMAIL = "noreply..."
REPORT_EMAIL_SUBJECT = 'CyBroWebScada: report'
SCGI_URL = "http://localhost/scgi/?"
SCGI_PORT = 4000
DATA_DIRECTORY = "/home/webscada/app/solar_cybro/data/"
CYBRO_SCGI_SERVER_DIRECTORY = "/home/webscada/app/scgi_server/"
SITE_URL = "https://perc.ddns.net/admin/webscada/"
PAGE_CACHE_VALIDITY = 3600 # seconds
ADMIN_MEDIA_PREFIX = '/media/admin/'
TIMEPLOT_INTERPOLATION = 4 # cumulative timeplot, defines how many bars (left and right) to take into account
STATIC_SETTINGS = {
"site_name": "Solar CyBro",
"contact_email": "mailto:info@cybrotech.hr?subject=SolarServer",
"head_caption": "solar plant supervisory system",
"footer_text": 'cybro web scada v%s, copyright © 2010-2013. <a href="http://www.cybrotech.co.uk/">Cybrotech Ltd.</a>' % version.WebSoftwareVersion,
"google_webmaster_tools_code": "",
"shortcut_icon": "/static/misc/favicon.ico",
}Zdaj npr. če naredite takšno bazo podatkov za SQL kot bom jaz in seveda ste prijavljeni v terminal z uporabnikom webscada:
sudo nano /home/webscada/app/scgi_server/src/sys_config.pyPopravi v svoje podatke SQL!!!
# database settings
DatabaseEngine = "mysql"
DatabaseHost = "localhost"
DatabaseName = "scada"
DatabaseUser = "scada"
DatabasePassword = "p90k7VOEaLppRx2a"
DatabaseDataLoggerSamplesTable = "measurements"
DatabaseDataLoggerAlarmsTable = "alarms"
DatabaseDataRelayDataTable = "relays"
DatabaseDataControllersTable = "controllers"Se pravi vi spremenite na bazi vaše podatke za SQL baza in uporabnik, katerega bomo zdaj ustvarli, mojem primeru za pi4 test kot sm rekel je:
DATABASE_NAME = 'scada'
DATABASE_USER = 'scada'
DATABASE_PASSWORD = 'p90k7VOEaLppRx2a' 13) Namestimo oz. Generiramo za WEBScado SQL bazo in uporabnika
Zdaj prvo zaženete spodnjo komando in odgovorite tako prvi odgovor je Y oz. yes (DA) in vsi ostali odgovori so N oz. no (NE):
sudo mysql_secure_installationZdaj se prijavite v SQL v.10.xx oz. Maria DB tako da vpišete vašo kodo za uporabnika webscada ali če boste namestili na drugega uporabnika pol vse direktive kjer je pri meni moj primer webscada spremenite z uporabnikom, ki ste ga generirali za WEB Scado:
sudo mysql --user=root --password=mojawebscada1234koda
## Se pravi kot je moja koda za test PI4 se pravi mojawebscada1234koda vi to samo zamenjate z vašo kdo, ki ste jo dali za uporabnika webscada oz. tistega uporabnika kjer bo scada nameščena karkoli!!!V mariaDB kopirajte spodnje direktive vse in kar z desnim miškinim kazalcem kliknite v terminal, ne pozabit spremenit vašo kodo lahko tudi ime baze in uporabnika po želji:
Za mariaDb ustvarite samo bazo in uporabnka ker dodelite vse privilegije pol omejite v phpmyadmin.
CREATE DATABASE scada;CREATE USER 'scada'@'localhost' IDENTIFIED BY 'p90k7VOEaLppRx2a';GRANT ALL PRIVILEGES ON scada.* to 'scada'@'localhost';FLUSH PRIVILEGES;
exit
in zdaj v račun webscada iz terminala naložite app že pripravljeno vse – zadnja verzija DDL mapa je dostopna samo če je vaše omrežje v allow:
cd /home/webscada/
wget https://perc.ddns.net/ddl/app.zip
unzip app.ziprm app.zip
setfacl -m u:www-data:--x /home/webscada/appsetfacl -R -m u:www-data:--- /home/webscada/app/*setfacl -R -m u:www-data:rwx /home/webscada/appsetfacl -R -m d:u:www-data:rwx /home/webscada/appchmod g+s /home/webscada/appsetfacl -R -m d:u:webscada:rwx /home/webscada/appchmod 755 /home/webscada/app/scgi_server/src/cybro_com_server.pychmod 755 /home/webscada/app/scgi_server/src/cybro_scgi_server.pychmod 755 /home/webscada/app/scgi_server/src/run_scgi_server.py
sudo mkdir /home/webscada/app/solar_cybro/data/cache
sudo mkdir /home/webscada/app/solar_cybro/data/media
sudo mkdir /home/webscada/app/solar_cybro/data/scripts
sudo mkdir /home/webscada/app/solar_cybro/data/analize
sudo nano /etc/rc.local
sudo -u webscada /home/webscada/app/scgi_server/src/run_scgi_server.py
cd /home/webscada/
app/scgi_server/src/cybro_scgi_server.py start
webscada@mojascada:~ $ app/scgi_server/src/cybro_scgi_server.py status
CybroScgiServer v2.3.3 (c) 2010-2014 Cybrotech Ltd. All rights reserved.
————————————————————————
CybroScgiServer is running.
sys.scgi_port_status: active
sys.scgi_request_count: 11550
sys.scgi_request_pending: 0
sys.server_version: 2.3.3
sys.server_uptime: 1:48:04
sys.cache_valid: 5
sys.cache_request: 2
sys.push_port_status: active
sys.push_count: 109
sys.push_list_count: 1
sys.push_ack_errors: 1
sys.push_list:
push message nad ip address:port status program alc program downloaded response
——————————————————————————————————-
2022-05-14 23:15:02 12133 89.212.137.96:61361 run ok ok 2022-05-14 21:48:52 63
——————————————————————————————————-
sys.udp_rx_count: 10636
sys.udp_tx_count: 10658
sys.abus_list:
nad abus total abus error last error at code bandwidth
——————————————————————————————————-
12133 10658 21 2022-05-14 20:57:44 tout 18.63%
——————————————————————————————————-
sys.datalogger_status: active
sys.datalogger_list:
type tags tasks trigger count last request at tags ok tags err status duration
——————————————————————————————————-
sample 39 4 317 2022-05-14 21:15:00 28 8 ok 75ms
alarm 9 1 108 2022-05-14 21:15:00 6 3 ok 53ms
event 27 3 6226 2022-05-14 21:15:07 6 6 ok 81ms
——————————————————————————————————-
webscada@mojascada:~ $
sudo /home/webscada/app/scgi_server/src/cybro_scgi_server.py restart
sudo /home/webscada/app/scgi_server/src/cybro_scgi_server.py restart
sudo /home/webscada/app/scgi_server/src/cybro_scgi_server.py stop
sudo /home/webscada/app/scgi_server/src/cybro_scgi_server.py start
sudo /home/webscada/app/scgi_server/src/cybro_scgi_server.py status
Goran Kociančič WEB Scada 2022 Raspbian 10 Linux Deluje vse razen Templates boste mogli posebej generirat v phpmyadmin tabelo, drugo vse dela – trenutna kopija ki jo poberete iz robotinal.si delajo templates pero ne delajo kontrolerji se jih ne da registrirat napaka!!!! Poberite to verzijo Testirana deluje na Ubuntu14-18-20 in Debian 9 10 11 in Raspbian 10 in 11 / 32 ali 64 bit testirano deluje vse kot mora!!!
 Za generirat templates če ne popravite v python skripta da dela za mariadb mysql pol lahko enostavno tako uredite problem!
Za generirat templates če ne popravite v python skripta da dela za mariadb mysql pol lahko enostavno tako uredite problem!
Prijevite se v phpmyadmin odprite scada bazo in poiščite templates kliknite na njega in zgoraj jeziček Vstavi dodaj po vrsi id 1, 2, za vsak template določiš npr ime kuhinja, centralna, sončna,…… Lahko pa razhroščite tudi tako da v python popravite ker Delbian 10 11 po defaultu uporablja MYSQL10 lahko si tudi namestite MYSQL8 in vam bo delalo vse!!!
CREATE DATABASE `bazasolar` DEFAULT CHARACTER SET utf8 COLLATE utf8_bin;
# Ali krajše samo:
create database bazasolar;
# Za menjat kodo SQL root - ni potrebno!!!!
SET PASSWORD FOR 'root'@'127.0.0.1' = PASSWORD('mojawebscada1234koda');
SET PASSWORD FOR 'root'@'::1' = PASSWORD('mojawebscada1234koda');
SET PASSWORD FOR 'root'@'localhost' = PASSWORD('mojawebscada1234koda');
# Ustvarit uporabnika SQL:
create user 'webscada'@'localhost' identified by 'MojaKodaSQL12345KarkoliWEBSCADA' WITH GRANT OPTION MAX_QUERIES_PER_HOUR 0 MAX_CONNECTIONS_PER_HOUR 0 MAX_UPDATES_PER_HOUR 0 MAX_USER_CONNECTIONS 0;
# Sprosti vse privilegije za bazo in uporabnika:
GRANT ALL PRIVILEGES ON `bazasolar` . * TO 'webscada'@'localhost';
# Ali krajše sprosti privilegije:
grant all privileges on bazasolar.* to 'webscada'@'localhost';
# Za konec še to in izhod....
flush privileges;
exit;
V phpmyadmin uvozite osnovne dve baze, to lahko tudi storite preko terminala:
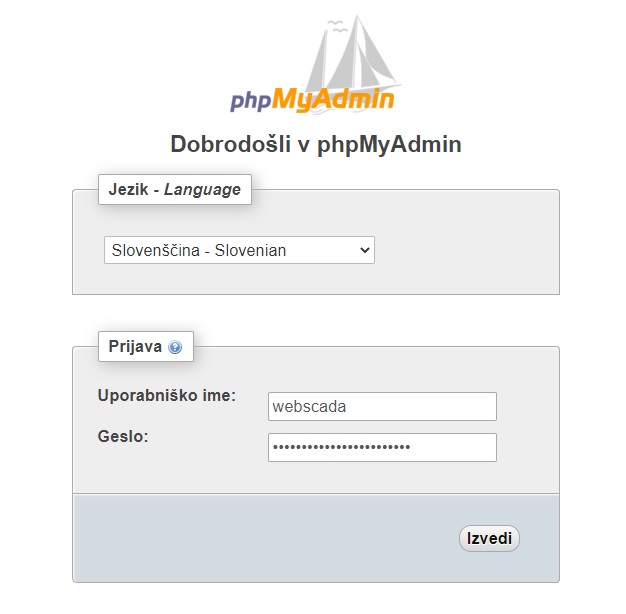
Zdaj če ste naredili po moje bazo in uporabnika gremo v phpmyadmin http://192.168.1.85/phpmyadmin/ in se prijavite tako z vašimi pristopnimi podatki za SQL uporabnika se pravi po moji varianti:
Uporabnik: webscada
Geslo: MojaKodaSQL12345KarkoliWEBSCADA
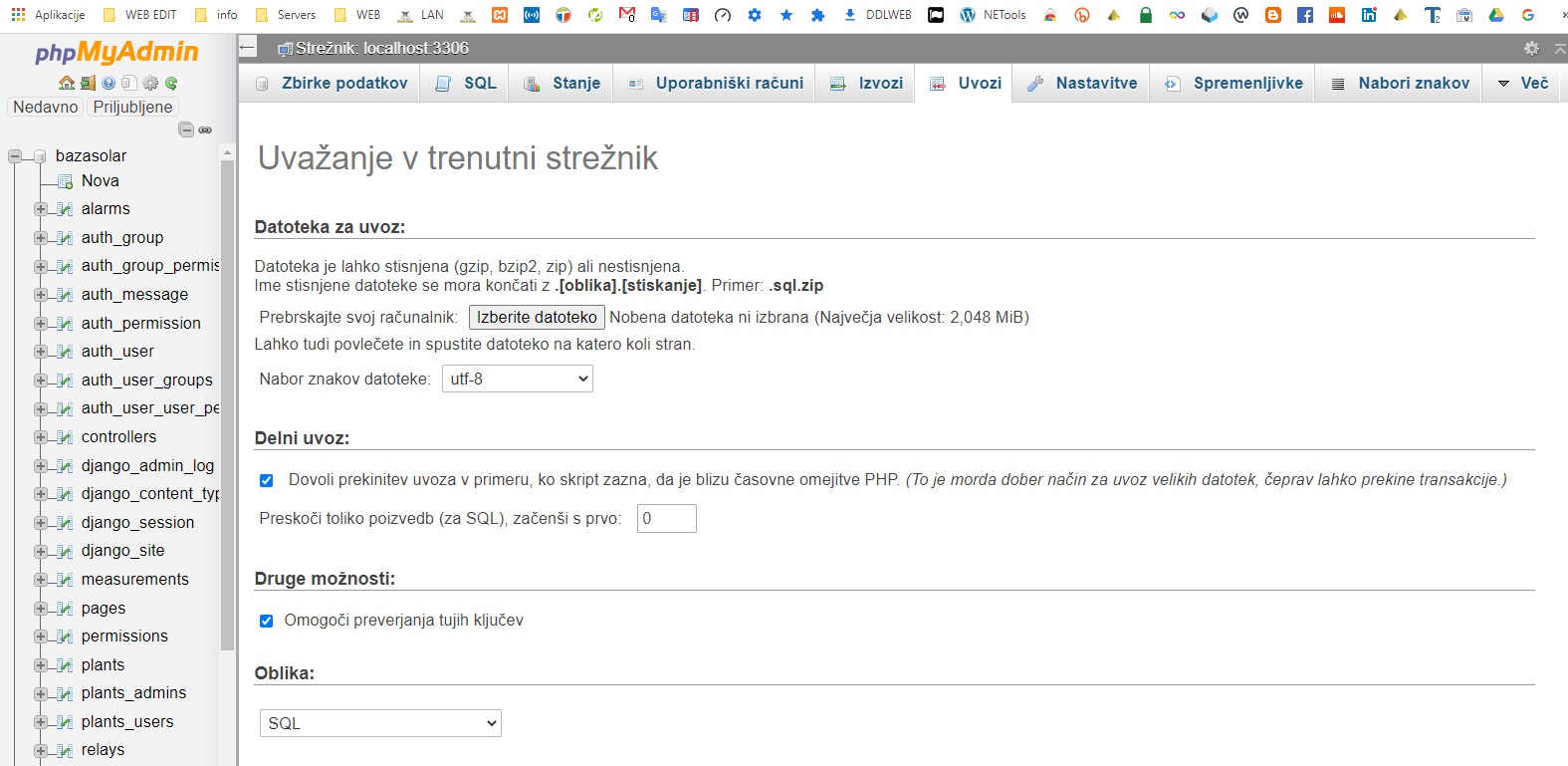
Zdaj pridemo v phpmyadmin in uvozimo bazo podatkov SQL od solar oz. ko ste odpakirali to datoteko zip “CyBroWebScada-v1.1.10-v2.3.0.zip” na vaš računalnik je v mapi DOC SQL baza podatkov od robotine katero moramo uvozit se pravi datoteke:
solar.sql
time_zone.sql
# Dodatne baza sql robotina.si
db_dump_v110.sql
db_upgrade_v110_to_v113.sql
db_upgrade_v113_to_v115.sql
db_upgrade_v114_to_v115.sql
Uvozimo v phpmyadmin v meniju uvozi ter kliknite izberi datoteko ter eno po eno izberete in kliknete spodnji gumb “Izvedi“
http://www.cybrotech.com/software-category/tools/
POZOR! DEBIAN 11 IN UBUNTU 20 NIMAJO VEČ TEH STARIH REPO! VEČINA MODULOV BOSTE MOGLI NAMESTIT IZ SOURCE – Apache WSCGI in MYSQL-python !!!
ZA PONOVNO ZAGNAT WSCGI SERVER UPORABITE V TERMINALU:
Zaženi na zadnje install django apps:
Software install - CybroTech WEB Scada:
$ sudo apt-get install apache2 mariadb-server mariadb-client php7.4 phpmyadmin libapache2-mod-wsgi acl ssh
$ sudo apt-get install python-django python-pip python-mysqldb
$ sudo pip install pytz
## na kondu Django v.13 obvezno ne novejših....
sudo apt install python-django python-pip python-mysqldb -y
sudo apt install libapache2-mod-php php-json php-fpm php-cli -y
sudo pip install django==1.3
sudo app/scgi_server/src/cybro_scgi_server.py restart
sudo app/scgi_server/src/cybro_scgi_server.py status
sudo app/scgi_server/src/cybro_scgi_server.py stop
sudo app/scgi_server/src/cybro_scgi_server.py startIN ZDAJ IMATE NAMEŠČENO SPLETNO APLIKACIJO WEB SCADA, OBIŠČETE NPR. VAŠ INTERNI IP RASPBERRY PI IN MOGLA BI SE VAM ODPRETI STRAN:
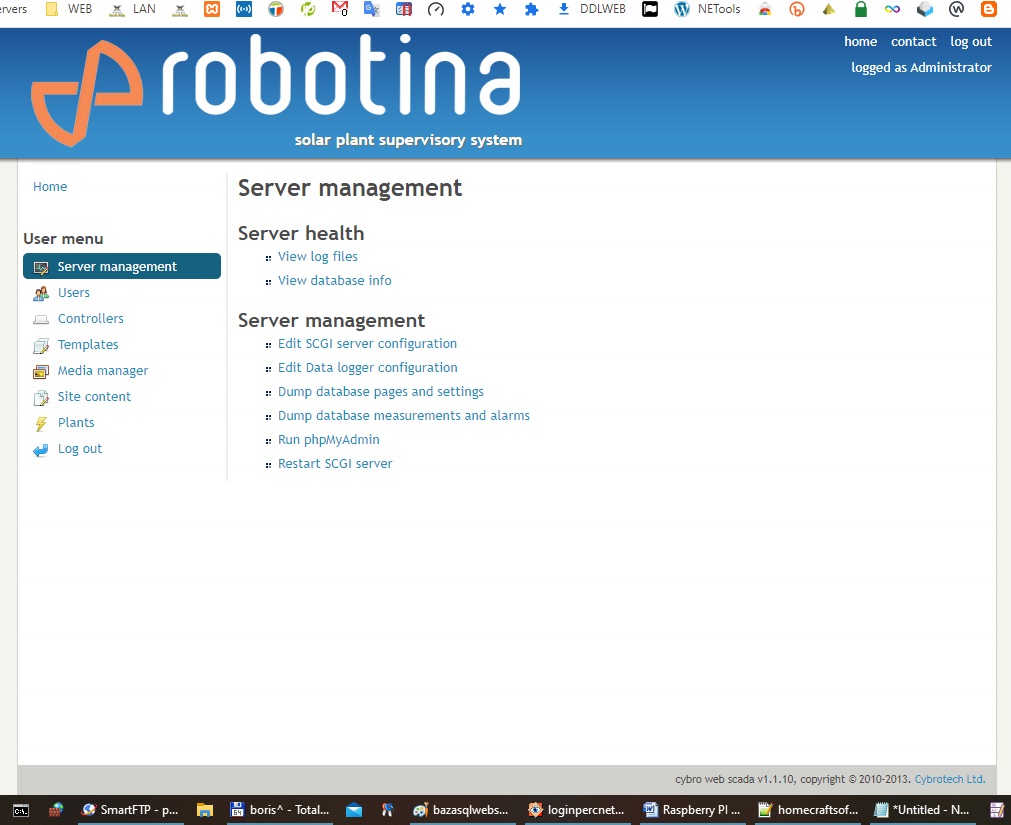 Prijavite se z Uporabnik: admin in Geslo: admin
Prijavite se z Uporabnik: admin in Geslo: admin
Za enkrat iz moje strani to bo vse, zaščitite primerno vaš serverček, npr. požarni zid ufw oz. nekomplicirani požarni zid od Ubuntu, deluje tudi za Raspbian Linux vendar ga odsvetujem za WEB Scado, uporabite direktive iptables katere sem vam predstavil zgoraj ne pozabit pol oddobrit porte 4000 in 8442 ter web porte 80 ter za ssl 443, jaz priporočam, še uporabo Fail2Ban spletne aplikacije, npr. za prijavni modul fail2ban zaščita priave za WEB Scada v mapi /etc/fail2ban/filter.d/ ustvarite nov filter tako da:
sudo nano /etc/fail2ban/filter.d/webscada.confKopirajte vse to v datoteko in shranite (# Prva in druga postavka je eno te isto in trejta ter četrta enako, v bistvu sem vam vpisal ali eno ali drugon ne igra vloge tisti, ki bodo falili prijavo jih zaklene!!!):
[Definition]
failregex = ^<HOST>.* "POST /accounts/login/.*
ignoreregex =Kopirate Zgornje Direktive shranite in v fail2ban jail.local aktivirate modul f2b za zaščito prijeve webscada tako, da na koncu datateke jail.local vpišete direktive za vklop filtera tako:
[webscada]
enabled = true
port = http,https
filter = webscada
logpath = %(apache_access_log)s
bantime = 24h
maxretry = 6
banaction = %(banaction_allports)sTe direktive za zaščito prijavnega mesa webscada pomenijo tako, se pravi kdorkoli bo falil prijavo 6 krat ga požarni zid zablokira za 24h to si sami parametrirajte po želji!!!
14) WEBMin – webmin.com – Jaz vam svetujem namestitve tega programa za lažje delo z strežnikom rasbian
Kaj je WEBmin ne bom razlagal to si poglejte na njihovi strani https://webmin.com/ PRAKTIČNO VAM BO OLAJŠALO DELO Z VAŠIM RASPBIAN SERVERJEM OZ. STREŽNIKOM, NE BOSTE POTREBOVALI VEČ TERMINALA OZ. PUTTY SAMO ŠE ZA SSL CERTIFIKATE IN GLAVNE NASTAVITVE BOSTE RABILI TERMINAL DRUGAČE VSE LAHKO NASTAVLJATE V WEBMIN ČISTO ENOSTAVNO – NE POTREBUJETE FTP SERVERJA, KER BOSTE VSE DELALI PREKO WEBMIN IN FILE MANAGER, BOLJ POENOSTAVLJENO, KOT BI IMELI WINDOWS SERVER, S TO RAZLIKO DA SE LINUX NIČ SAM NE NASTAVI!!!!
GREMO NAMESTIT WEBMIN TAKO DA V TERMINALU ZAŽGETE TO KOMANDO OZ. DIREKTIVO:
sudo nano /etc/apt/sources.listČiso na koncu kopirajte to direktivo:
deb https://download.webmin.com/download/repository sarge contribDa, Sarge je stara različica Debiana, vendar se to skladišče redno posodablja
Zdaj morate namestiti ključ GPG, ki ustreza temu repozitoriju oz. skladišču zažgite v terminalu spodnje komandi:
sudo wget http://www.webmin.com/jcameron-key.asc
sudo apt-key add jcameron-key.asc
Zdaj pa še za konec namestimo webmin tako da v terminalu kopiramo te komande oz. direktive sorry sm primorec ne uporabljam dvojine:
sudo apt update
sudo apt install webmin -y
KO STE NAMESTILI WEBMIN GA ŠTARTATE OZ. SE PRIJAVITE NA NJEGA TAKO DA V VAŠ BRSKALNIK (Chrome, Opera, Internet Explorer, Mozzila,…..) VPIŠETE:
https://ipraspberry:10000/
npr. https://192.168.1.82:10000
Potrdite samoregistrirani SSL od WEBMin in se prijavite npr. z uporabnikom WEBSCADA in GESLOMZdaj namestite še ta program za nadgradno npr. tem webmin in ostalo:
sudo apt-get install git -yPol če boste implementirali za vaš server npr. SSL Certifikat CertBot pa boste v webmin meni “Webmin Configuration” namestili še modul CertBot tako, da kliknete na ikono Webmin Modules in v polje “From HTTP or FTP URL” boste vpisali oz. kopirali spodnjo povezavo URL ter kliknili Install Module
http://cdn.acugis.com/certbot-webmin-module/certbot.wbm.gzZdaj vse namestitve modulov, lahko namestite preko webmin z klikom na željeni modul npr. apache, sql, ftp (ne rabi),….. Ampak jaz vam bom tu dalje vse pokazal za terminal namestitev dodatnih modulov!
15) Namestiom UFW nekomplicirani požarni zid za linux – ODSVETUJEM ZA UPORABNIKE WEBSCADA:
Namestite ufw zaženi v terminalu: (ZA RASPBERRY PI WEB SCADA SMO ŽE VSE ZAŠČITILI Z IPTABLES LINUX POŽARNIM ZIDOM – NE RABITE, ZA DOMAČE UPORABNIKE ZAPRTA OMREŽJA LAHKO BREZ PROBLEMOV NAMESTITE ŠE UFW PO ŽELJI – UFW to je od Ubuntu Linux “Nekomplicirani Požarni Zid” vendar ga vam jaz osebno odsvetujem, še posebej če imate večje število kontrolerjev po Sloveniji ali tujini npr. za nadzor poslovnih prostorov, vikend hiš, stanovanj, itd…)
Ta požarni zid vam odsvetujem za WEB Scado, ker vam bo blokiral kontrolerje oz. vam ne bo dodelil UDP porta preko porta 8442 ne gelde, če le tega posredujete v splet!!! Uporabite iptables z direktivami, ki sem vam jih pripravil!!!
###Glavna direktiva iptables odpri porte preko iptables tako:
sudo iptables -A INPUT -p tcp -m tcp -m multiport -j ACCEPT --dports 22,80,443,4000,8442
sudo iptables -A INPUT -p udp -m udp --dport 1024:65535 --sport 8442 -j ACCEPT
## ali posamezni port primer pred vsakim -A dodate sudo iptables:
-A INPUT -p tcp -m tcp --dport 21 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 25 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 80 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 443 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 465 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 587 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 143 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 993 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 110 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 995 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 4000 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8442 -j ACCEPT
Lastne nastavitve primer vBox WEB Scada Debian 10+11 / 32 ter 64bit Shema: Router IP 192.168.1.1 Server IP 192.168.1.100 Main Server Server IP 192.168.1.111 Multimedia Server IP 192.168.1.123 RPI-10 Server IP 192.168.1.222 WindowsNT ### Namestitev UFW nekomplicirani požarni zid - Ni dobro za WEB Scado če ste admin strank BLOKIRA UDP PORT IN VAM NE BO DODELILO NASLOVA, UPORABITE IPTABLES, KI SEM GA PRIPRAVIL ZA WEBSCADA!!!
sudo apt install ufw
sudo ufw enable -y
sudo ufw allow 80
sudo ufw allow 443
sudo ufw limit ssh/tcp
sudo ufw allow 25
sudo ufw allow 465
sudo ufw allow 587
sudo ufw allow 143
sudo ufw allow 993
sudo ufw allow 110
sudo ufw allow 995
sudo ufw allow 4000
sudo ufw allow 8442
sudo ufw allow 10000
#sudo ufw allow 20000
sudo ufw allow from 192.168.1.10 port 22
# Tvoj ip local npr. PC s katerega dostopate v terminal
Noip.com Namestitev aplikacije dinamični internet – DDNS:
### kot root@webscada: vaš hostname:
cd /usr/local/src/
sudo wget http://www.no-ip.com/client/linux/noip-duc-linux.tar.gz
tar xf noip-duc-linux.tar.gz
sudo rm noip-duc-linux.tar.gz
cd noip-2.1.9-1/
sudo make install
cd /etc/
sudo nano rc.local
## ****rc.local...
sudo noip2
# Shrani
sudo shutdown -r now
sudo noip2 -S
16) Namestitev Požarnega zida za spletne aplikacije – fail2ban:
V terminalu zaženite spodnje komande:
sudo apt install fail2ban -y
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
sudo nano /etc/fail2ban/jail.local
enabled = true
filter = apache-badbots
# Za vklopit modul kot je zgoraj enable in ime filtra!!!
ls /etc/fail2ban/filter.d/
sudo service fail2ban restart
sudo service fail2ban statusKonfiguracija Fail2Ban za WEB Scado – sudo nano /etc/fail2ban/fail2ban.conf:
Konfiguracija fail2ban modulov – sudo nano /etc/fail2ban/local.jail:
Poglejte prispevek: https://oglasi.hopto.org/fail2ban-linux-pozarni-zid-nastavitev-za-wordpress-best-opcija-iptables-ufw/
Fail2Ban konfiguracija modulov: Debian/Raspbian/Ubuntu Linux: Tukaj objava!!!!
Poglejte si še spodnji link SCADA ZA PI4 Referenca, druga varianta postavitve pametne hiše:
http://www.scadasoftware.net/systems/scadaraspberrypi.html














PSM ITALY‚Radio